09 application security fundamentals - part 2 - security mechanisms - logging
- 1. LOGGING Security Mechanism: Authentication Authorization Session Management Data Validation Error Handling Logging Encryption
- 2. Logging Core Concepts What happened? Who was doing what, when & where? important to have an application log in addition to the server log Not just bugs & error events… Determine what security events should be auditable. For example: • Use of administrative functions • Login success & failures • Password reset attempts • Password changes
- 3. Logging Words to Live By Avoid logging sensitive data (e.g., passwords) Beware of logging tainted data to the logs Beware of logging excessive data Beware of potential log spoofing
- 4. Logging Words to Live By: #1 The problem – Information written to log files can be of a sensitive nature and give valuable guidance to an attacker or expose sensitive user information. Avoid logging sensitive data (e.g., passwords)
- 5. Real World Example – Logging Sensitive Data
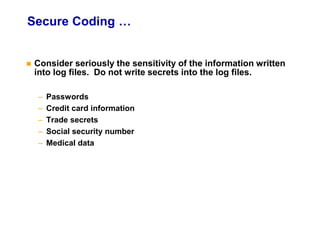
- 6. Secure Coding … Consider seriously the sensitivity of the information written into log files. Do not write secrets into the log files. – Passwords – Credit card information – Trade secrets – Social security number – Medical data
- 7. Logging Words to Live By: #2 The problem – The software does not neutralize or incorrectly neutralizes output that is written to logs. Beware logging tainted data to the logs
- 8. Logging Words to Live By: #3 The problem – The software logs too much information, making log files hard to process and possibly hindering recovery efforts or forensic analysis after an attack. Beware of logging excessive data
- 9. Logging Words to Live By: #4 The problem – The software uses CRLF (carriage return line feeds) as a special element, e.g., to separate lines or records, but it does neutralize or incorrectly neutralizes CRLF sequences from inputs. Beware of potential log spoofing
- 10. Real World Example – Log Spoofing CVE-2006-4624:
- 11. Secure Coding … Appropriately filter or quote CRLF sequences in user- controlled input. 1 string streetAddress = request.getParameter("streetAddress")); 2 3 if (streetAddress.length() > 150) error(); 4 streetAddress = RemoveCarriageReturns(streetAddress); 5 6 logger.info("User's street address: " + streetAddress);