Easy public-private-keys-strong-authentication-using-u2 f
- 1. Easy public/private keys usage protected with strong authentication, using U2F/UAF from theBased on documentation and presentation from fidoalliance, Yubicoand GoogleRump Session, 6 November 2014Application Security Forum Western Switzerland André Liechti (@andreliechti, @multiOTP) Last update : 2014-12-09
- 2. FIDO Alliance, whoisthat? FIDO (Fast IDentityOnline) 2007 PayPal launched Security Key (classic OTP token) Low adoption rate, because harder to use for end users Late 2009 Ramesh Kesanupalli(CTO of Validity Sensors) visited Michael Barrett (PayPal's CISO). Barretinsisted on two things: solution based on a (future) industry standard must support Validity’s hardware and also their competitors July 2012 FIDO Alliance nominallyformedPayPal, Lenovo, NokNokLabs, Validity Sensors, Infineon, and Agnitio February 2013 Alliance publicly launched and growing. Google, Yubico, ... 2014-11-06 2
- 3. FIDO Alliance members(150 in November2014) Board Level 21 members : Alibaba Group, ARM, Bank of America, BlackBerry, CrucialTec, Discover, Google, IdentityX, Lenovo, MasterCard, Microsoft, NokNokLabs, NXP, OberthurTechnologies, PayPal, Qualcomm, RSA, Samsung, Synpatics, Visa, Yubico Sponsor Level 48 members Associate Level 81 members 2014-11-06 3
- 4. FIDO Alliance mission The Mission of the FIDO Alliance is to change the nature of online authentication by: Developing technical specifications that define an open, scalable, interoperable set of mechanisms that reduce the reliance on passwords to authenticate users. Operating industry programs to help ensure successful worldwide adoption of the Specifications. Submitting mature technical Specification(s) to recognized standards development organization(s) for formal standardization. 2014-11-06 4
- 5. Online Authentication: whatU2F/UAF are tryingto solve? Avoid asking users for (secure?) passwords only because: same password is reused for a lot of services phishing is still working well plenty of hardware and software keyloggersare available Existing solutions have known problems: Most of hardware devices are fragile, you must have one for each service, you have battery issues SMS costs are not negligible, you can be out of coverage End user don’t always understand how to use it Some phishing attacks are still possible 2014-11-06 5
- 6. UAF : passwordlessexperience UAF: Universal Authentication Framework Passwordlessexperience 2014-11-06 6
- 7. U2F : second factor experience U2F: Universal Second Factor protocol Second factor experience 2014-11-06 7
- 8. U2F Protocol Core Idea: Standard Public Key Cryptography User's device mints new key pair, gives public key to server Server asks user's device to sign data to verify the user One device, many services -“Bring Your Own Authenticator” Design Considerations: Privacy: Site SpecificKeys, No unique ID per device Security: No phishing, Man-In-The-Middles Trust: User decide what authenticator to use Pragmatics: Affordabletoday Usability: No delays, Fast crypto in device 2014-11-06 8
- 9. U2F flow 2014-11-06 9
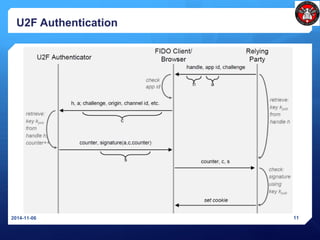
- 10. U2F Registration 2014-11-06 10
- 12. U2F and MITM attack The client send: I promise a user was here The server challenge was: KSDJsdASAS-AIS_Me The originwas: accounts.acme.com The TLS connection state was: 345567 MITM attackdetection Origin mismatch for key handle Incorrect origin name ChannelIDmismatch 2014-11-06 12
- 13. What if I want to accept U2F logins for my service? Server: Implement registration flow decide how to handle attestation certificates verify registration response store public key, key handle with user account Server: Implement login flow check username/password, look up key handle verify authentication response (origin, signature, counter, …) Check your account recovery flow 2014-11-06 13
- 14. Yubicoimplementation details “ There is no practical limit to the U2F secured services the YubiKeycan be associated with. During the registration process, the key pairs are generated on the device (secure element) but the key pairs are not stored on the YubiKey. Instead, the key pair (public key and encrypted private key) are stored by each relying party/service that initiated the registration. Therefore, this approach allows for an unlimited number of services to be associated with the YubiKey. ” 2014-11-06 14
- 15. U2F demo with YubikeyFIDO U2F Security Key http://demo.yubico.com/u2f 2014-11-06 15