Implement fingerprint authentication for employee automation system
- 1. International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017 Issue 09, Volume 4 (September2017) www.ijiris.com __________________________________________________________________________________________________ IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651 Indexcopernicus: (ICV 2015): 73.48 © 2014- 17, IJIRIS- All Rights Reserved Page - 5 - IMPLEMENT FINGERPRINT AUTHENTICATION FOR EMPLOYEE AUTOMATION SYSTEM Dr.Md.Mijanur Rahman Associate Professor, Dept. of Computer Science and Engineering Jatiya Kabi Kazi Nazrul Islam University, Bangladesh. mijanjkkniu@gmail.com Tanjarul Islam Mishu MS Student, Dept. of Computer Science and Engineering Jatiya Kabi Kazi Nazrul Islam University, Bangladesh. tanjarul26@gmail.com Md. Saiful Islam MS Student, Dept. of Computer Science and Engineering Jatiya Kabi Kazi Nazrul Islam University, Bangladesh. saifulislamcse@yahoo.com Md. Shoaib Akanda MS Student, Dept. of Computer Science and Engineering Jatiya Kabi Kazi Nazrul Islam University, Bangladesh. shoaib.akanda@gmail.com Manuscript History Number: IJIRIS/RS/Vol.04/Issue09/SPIS10080 DOI: 10.26562/IJIRIS.2017.SPIS10080 Received: 17, August 2017 Final Correction: 25, August 2017 Final Accepted: 03, September 2017 Published: September 2017 Citation: Rahman, D.; Mishu, T. I.; Islam, M. & Akanda, M. (2017), 'IMPLEMENT FINGERPRINT AUTHENTICATION FOR EMPLOYEE AUTOMATION SYSTEM', Master's thesis, Jatiya Kabi Kazi Nazrul Islam University, Bangladesh. Editor: Dr.A.Arul L.S, Chief Editor, IJIRIS, AM Publications, India Copyright: ©2017 This is an open access article distributed under the terms of the Creative Commons Attribution License, Which Permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited Abstract- The project work is concerned with the implementation of biometric fingerprint authentication system which is an automated method of verifying a match between two human fingerprints for validating identity. The modern computer security is a battle between high security and low friction. Developers want users to use unique, complicated passwords for their apps to increase security. Employee Automation System is designed to ensure that the organization is equipped with the right level of human resource tracking for each separate department of the organization. The main feature of Employee Automation System is time tracking for employees. The system is implemented based on biometric fingerprint features that identifies certain or specific employee. The system can be accessible from remote network. The developed system also includes the employee fingerprint verification, employee attendance, employee tracking, employee leave, and salary payment and promotion modules. The operational activities of the system are accessed or controlled by three users, like Admin, Operator and Employee. The admin can access all the features, whereas the operator panel is designed to run the software in office time and takes fingerprint attendance. The employee panel is accessible by employee that shows profile information, last fingerprint attendance access, leaving/absent status of that month. The system is designed with client-server model and software methodology. Keywords: Automation System, Authentication, Biometric Features, Fingerprint Enrollment and Verification.
- 2. International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017 Issue 09, Volume 4 (September2017) www.ijiris.com __________________________________________________________________________________________________ IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651 Indexcopernicus: (ICV 2015): 73.48 © 2014- 17, IJIRIS- All Rights Reserved Page - 6 - I. INTRODUCTION Modern security is a battle between high security and low friction [1]. Developers want users to use unique, complicated passwords for their apps to increase security. One way to combine both performance and security is to take advantage of fingerprint sensors that are now prevalent on high-end smart phones and other mobile devices. Fingerprints have a number of benefits over passwords [2], such as, (i) modern capacitive touch fingerprint sensors recognize the fingerprint and unlock in less than a second, quicker than inputting an extensive password; (ii) fingerprints are unique, impossible to guess, and difficult to fake without significant effort; (iii) Complex passwords are hard to remember, leading to the majority of people reusing passwords on multiple sites. As a physical feature, fingerprints are unforgettable. An automation system is a desktop application [3], which gives facility available for every organization. The information about an employee from enter into to leave from the organization are recorded. When an employee enters the company he/she is verified by fingerprint verification [4, 5]. Then the employees go their work place to carry out their duties and the working time is started. Employees leave the office also by using the fingerprint verification. Monthly salary and other benefits are calculated by the system using their information. All the works are properly documented as weekly or monthly reports. Attendance report shows employees record like holidays, present days, absent days etc. This report is generated by SAP Crystal Report [6].We have collected the devices, the fingerprint scanner that is required to develop security system. According to the requirements, we first design the structure of the system. The system can overcome all the limitations of the existing system. The system provides proper security and reduces the complexity of the manual work. II. BIOMETRIC FINGERPRINT AUTHENTICATION APPROACH Biometric Fingerprint Authentication [7] is an automated method of verifying a match between two human fingerprints for validating identity. That is, the authentication systems provide a means of verifying identity by collecting information about unique human characteristics and comparing that information to previously- submitted data. BioID [8] incorporates a biometric sensor that collects information about users’ unique fingerprints and a matcher that facilitates decisions on whether access should be granted to the user based on data collected from the sensor. The user places a finger on the external surface of the sensor, or platen, and relevant information is quickly extracted and transformed into a digital representation of the user’s fingerprint, or template. A template is not an image of a fingerprint, and fingerprint images cannot be restored from the encoded templates. The user’s template is compared to the reference template the authorized user provided during an initial enrollment process. If the two templates match, the user is granted access. The entire process, from finger placement to match result, takes place in approximately two seconds with the BioID fingerprint identification system. III. EMPLOYEE AUTOMATION SYSTEM The system is very simple in design and to implement. The system requires very low system resources and the system worked in almost all configurations. The proposed employee automation system (see Figure-1) includes the following major modules integrated with each others: Figure 1: Modules of Proposed Employee Automation System.
- 3. International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017 Issue 09, Volume 4 (September2017) www.ijiris.com __________________________________________________________________________________________________ IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651 Indexcopernicus: (ICV 2015): 73.48 © 2014- 17, IJIRIS- All Rights Reserved Page - 7 - a) Employee Management System: The employee management system helps to keep a detailed record including the fingerprints of all the employees working in the institution. It is important for the institution to verify the employee before hiring and the employee management system asks the employee to enter all relevant data and stores all required documents in the database. b) Employee Attendance Management System: The employee attendance management system is a module which is primarily used to record the daily attendance of the employee. The employee attendance management system can be integrated with any smart card or fingerprint module which instantly records the presence of the employee and updates it in the attendance system. c) Employee Leave Management System: The employee leave management module is designed to keep a track of the leaves an employee takes with a term or financial year. Every institute has a fixed earned leaves and sick leaves policy and the leave management system helps in keeping a track of these leaves as when they are exercised by the employee. d) Employee Performance Management Software: Keeping track of the performance of an employee is of utmost importance to any organization. The employee performance management system helps the institution record employee performance details and analyzes their performance over a period of time. e) Employee Payroll System: The employee payroll system has been designed to record payment and salary details of the employee. The salary slip, provident fund details and other tax related information is recorded on this employee payroll system for ease of access. f) Employee Monitoring Software: Starting from attendance to leaves, all day to day information of the employee is recorded on the employee monitoring software. IV. SYSTEM ANALYSIS AND DESIGN The analysis and design phase provides the developing process of employee automation system including Software Requirement Specification (SRS) [9,10]. Figure 2: ER Diagram of the Proposed System The SRS part to provide complete description and overview of system requirement before the developing process is carried out. Besides that, the data flow diagram (DFD) [11] provides a view of how the system flows that able to increase the efficiency and effectiveness to achieve system objectives. The system is designed to satisfy the user requirements based on analysis of the system. In system design the logical model is moved to the physical aspects. The requirements identified in the requirements analysis phase are transformed into a system design document that accurately describes the design of the system. The database design is an important part of the software development. The data are manipulated and stored in database and then generated output data such as listing absent employee and count currently working employees, giving status of department, payment, promotion, monthly attendance Report etc. The entity-relationship (ER) diagram [12] and the database schema design [12] are shown in Figure-2 and Figure-3, respectively.
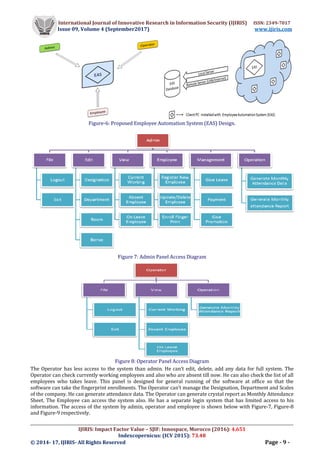
- 4. International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017 Issue 09, Volume 4 (September2017) www.ijiris.com __________________________________________________________________________________________________ IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651 Indexcopernicus: (ICV 2015): 73.48 © 2014- 17, IJIRIS- All Rights Reserved Page - 8 - Figure 3: Database Schema Diagram of the Proposed System. V. FINGERPRINT ENROLLMENT AND VERIFICATION At the time of employee registration, the New Employee is asked to give their fingerprint. The finger print is taken with fingerprint index [13], employee id, it takes three times to ensure the finger. The fingerprint scanner device scan and generate a finger print template [14], the process in known as fingerprint enrollment (see Figure-4). The template is stored in the database and is used for employee verification (see Figure-5). After the completing of enrollment, employee is verified when he/she tries to enter in office. When the employee is verified, a record is stored in database. Figure 4: Fingerprint Enrollment Figure 5: Fingerprint Verification VI. PROPOSED SYSTEM DESIGN In this project work, the system is designed with three parts or panels; such Admin Panel, Operator Panel and Employee Panel (see Figure-6). The admin has the super power of all access. The admin can edit, delete, add all data for full system. He can check currently working employees and also who are absent till now. He can also check the list of all employees who takes leave. The admin can manage the Designation, Department and Scales of Salary Payment of the company. He can also give leave to a limit of date for an employee, can give promotion, can pay employee, can generate attendance data. The admin can generate crystal report as Monthly Attendance Sheet.
- 5. International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017 Issue 09, Volume 4 (September2017) www.ijiris.com __________________________________________________________________________________________________ IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651 Indexcopernicus: (ICV 2015): 73.48 © 2014- 17, IJIRIS- All Rights Reserved Page - 9 - Figure-6: Proposed Employee Automation System (EAS) Design. Figure 7: Admin Panel Access Diagram Figure 8: Operator Panel Access Diagram The Operator has less access to the system than admin. He can’t edit, delete, add any data for full system. The Operator can check currently working employees and also who are absent till now. He can also check the list of all employees who takes leave. This panel is designed for general running of the software at office so that the software can take the fingerprint enrollments. The Operator can’t manage the Designation, Department and Scales of the company. He can generate attendance data. The Operator can generate crystal report as Monthly Attendance Sheet. The Employee can access the system also. He has a separate login system that has limited access to his information. The access of the system by admin, operator and employee is shown below with Figure-7, Figure-8 and Figure-9 respectively.
- 6. International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017 Issue 09, Volume 4 (September2017) www.ijiris.com __________________________________________________________________________________________________ IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651 Indexcopernicus: (ICV 2015): 73.48 © 2014- 17, IJIRIS- All Rights Reserved Page - 10 - Figure 9: Employee Panel Access Diagram VII. EXPERIMENTAL RESULTS An Employee Automation System accurately captured all time worked. It calculated employee started time and ending time. It also calculated how much time he/she works. The proposed system created central database that can be accessed throughout the company and share multiple computer via LAN. The system calculated salary for every employee based on their working days. Employee automation system used fingerprint verification for every person in the office that secures the organization/company. The system generated reports that show working days, absent days, working hours, holydays and working percentage. The software system included three parts, Admin login, Operator login, Employee login, discussed earlier. Only admin can access like as operator and employee but operator and employee can’t access as admin Figure 10: Main Window Figure 11: Employee Detected by Finger Print Scanner
- 7. International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017 Issue 09, Volume 4 (September2017) www.ijiris.com __________________________________________________________________________________________________ IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651 Indexcopernicus: (ICV 2015): 73.48 © 2014- 17, IJIRIS- All Rights Reserved Page - 11 - The system can register new employee update/delete employee status. Every employee can show his/her personal details. Without this system it’s tedious job for the human resource department to keep track of each and every employee and even harder for a project manager to assign tasks to the project team. The front-end of the software system is shown in Figure-10. It is the home window or main window which has a lot of features. It gives the status of currently working people, headlines of the messages, shows departmentwise information. It also shows the last employee detected and his time of attendance record, as shown in Figure-11. Figure 12 : Register New Employee (a) Finger Selection (b) Selected Finger Print Enroll Figure 13: Register Finger Print for New Employee Figure 14: Update Employee Information
- 8. International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017 Issue 09, Volume 4 (September2017) www.ijiris.com __________________________________________________________________________________________________ IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651 Indexcopernicus: (ICV 2015): 73.48 © 2014- 17, IJIRIS- All Rights Reserved Page - 12 - At any time, the home or main window connects the Finger print device, track the input fingerprint and match it to the stored database for verification. The registration of an employe includes two forms, as shown in Figure-12 and Figure-13. The register form takes name, father name, NID [15] etc. and store the information (see Figure-12). After that a new finger enrollment form comes and take the finger print of the new employee. The fingerprint register form takes three times of any one of ten fingers of an employe at a time (see Figure-14). After getting the finger print templates it stores them to Database. The system can easily update the employee’s information and fingerprint (see Figure-14). VIII. CONCLUSION Modern security is a battle between high security and low friction. Developers want users to use unique, complicated passwords for their apps to increase security. One way to combine both performance and security is to take advantage of fingerprint features that are now prevalent on high-end smart phones and other mobile devices. Because, fingerprint features have a number of benefits over passwords, such as, performance, security, permanence, etc. This is really authentic news that last couple of year many sensors device like finger print, eye/image detection, punch card system are available in Bangladesh using this many organization secure their system. More organizations are going to establish their business using this secure system for that they easily maintain their employee securely. This project work is aimed to develop an Employee automation system using fingerprint authentication. In future the system will combine with a secondary authentication scheme such as a secure PIN, so that; it will enhance security for the application and ensure the authenticity of the user. This system will be further developed with some additional features of original fingerprint images processing in employee automation system. REFERENCES 1. Grzegorz Kowalik, “Automation of Desktop Applications”, https://www.future-processing.pl/blog/automation- of-desktop-applications/, May 2014. 2. Sonali S. Gahukar, Gargi S. Phadke, “Safeguarding Confidentiality by Fingerprint Combination”, International Journal of Advanced Technology in Engineering and Science, Vol.4, Issue. 08, August 2016. 3. Diego Poza, “Fingerprint Authentication: High Security and Low Friction”, https://auth0.com/blog/how- fingerprint-auth-gives-you-security/, May 2016. 4. L. O'Gorman, “Overview of Fingerprint Verification Technologies”, Elsevier Information Security Technical Report, Vol. 3, No. 1, 1998. 5. Danny Thakkar, “Fingerprint Verification vs. Fingerprint Identification”, http://www.touchngoid.com/fingerprint-verification-vs-fingerprint-identification/, February 2016. 6. Peck, George, “Crystal Reports 2008: The Complete Reference”, McGraw-Hill Osborne Media.Pg. 968, ISBN 0- 07-159098-6, June 2008. 7. Er.Manu Kumar Garg, Er.Harish Bansal, “Review on Fingerprint Recognition System Using Minutiae Estimation”, International Journal of Research in Information Technology (IJRIT), Volume 1, Issue 7, July, 2013, Pg. 74-78. 8. BioID fingerprint identification system: The next generation technology,© 2010 CareFusion Corporation or one of its subsidiaries, carefusion.com, San Diego, CA. 9. Bourque P,Fairley R.E. (2014). “Guide to the Software Engineering Body of Knowledge (SWEBOK)”, IEEE Computer Society. Retrieved 17 July 2014. 10.Jump up, “Software requirements specification helps to protect IT projects from failure”. Retrieved 19 December 2016. 11.Bruza, P. D., Van der Weide, Th. P., “The Semantics of Data Flow Diagrams”, University of Nijmegen, 1993. 12.Chen Peter, “The Entity-Relationship Model - Toward a Unified View of Data”, ACM Transactions on Database Systems, Vol.1 (1): 9–36. doi:10.1145/320434.320440, March 1976. 13.Pooja A. Parmar and Sheshang D. Degadwala, “Fingerprint Indexing Approaches for Biometric Database: A Review”, International Journal of Computer Applications, Vol.130 (13), November 2010. 14.Le Hoang Thai, Ha Nhat Tam, “Fingerprint recognition using standardized fingerprint model”, IJCSI International Journal of Computer Science Issues, Vol.7, Issue 3, No 7, May 2010. 15.NID Services, National Identity Registration Wing, Election Commission Bangladesh. “http://www.nidw.gov.bd/index.php?option=com_content&view=featured&Itemid=435&lang=en”.

![International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017
Issue 09, Volume 4 (September2017) www.ijiris.com
__________________________________________________________________________________________________
IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651
Indexcopernicus: (ICV 2015): 73.48
© 2014- 17, IJIRIS- All Rights Reserved Page - 6 -
I. INTRODUCTION
Modern security is a battle between high security and low friction [1]. Developers want users to use unique,
complicated passwords for their apps to increase security. One way to combine both performance and security is
to take advantage of fingerprint sensors that are now prevalent on high-end smart phones and other mobile
devices. Fingerprints have a number of benefits over passwords [2], such as, (i) modern capacitive touch
fingerprint sensors recognize the fingerprint and unlock in less than a second, quicker than inputting an extensive
password; (ii) fingerprints are unique, impossible to guess, and difficult to fake without significant effort; (iii)
Complex passwords are hard to remember, leading to the majority of people reusing passwords on multiple sites.
As a physical feature, fingerprints are unforgettable. An automation system is a desktop application [3], which
gives facility available for every organization. The information about an employee from enter into to leave from
the organization are recorded. When an employee enters the company he/she is verified by fingerprint
verification [4, 5]. Then the employees go their work place to carry out their duties and the working time is
started. Employees leave the office also by using the fingerprint verification. Monthly salary and other benefits are
calculated by the system using their information. All the works are properly documented as weekly or monthly
reports. Attendance report shows employees record like holidays, present days, absent days etc. This report is
generated by SAP Crystal Report [6].We have collected the devices, the fingerprint scanner that is required to
develop security system. According to the requirements, we first design the structure of the system. The system
can overcome all the limitations of the existing system. The system provides proper security and reduces the
complexity of the manual work.
II. BIOMETRIC FINGERPRINT AUTHENTICATION APPROACH
Biometric Fingerprint Authentication [7] is an automated method of verifying a match between two human
fingerprints for validating identity. That is, the authentication systems provide a means of verifying identity by
collecting information about unique human characteristics and comparing that information to previously-
submitted data. BioID [8] incorporates a biometric sensor that collects information about users’ unique
fingerprints and a matcher that facilitates decisions on whether access should be granted to the user based on data
collected from the sensor. The user places a finger on the external surface of the sensor, or platen, and relevant
information is quickly extracted and transformed into a digital representation of the user’s fingerprint, or
template. A template is not an image of a fingerprint, and fingerprint images cannot be restored from the encoded
templates. The user’s template is compared to the reference template the authorized user provided during an
initial enrollment process. If the two templates match, the user is granted access. The entire process, from finger
placement to match result, takes place in approximately two seconds with the BioID fingerprint identification
system.
III. EMPLOYEE AUTOMATION SYSTEM
The system is very simple in design and to implement. The system requires very low system resources and the
system worked in almost all configurations. The proposed employee automation system (see Figure-1) includes
the following major modules integrated with each others:
Figure 1: Modules of Proposed Employee Automation System.](https://image.slidesharecdn.com/implementfingerprintauthenticationforemployeeautomationsystem-170924032313/85/Implement-fingerprint-authentication-for-employee-automation-system-2-320.jpg)
![International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017
Issue 09, Volume 4 (September2017) www.ijiris.com
__________________________________________________________________________________________________
IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651
Indexcopernicus: (ICV 2015): 73.48
© 2014- 17, IJIRIS- All Rights Reserved Page - 7 -
a) Employee Management System: The employee management system helps to keep a detailed record including
the fingerprints of all the employees working in the institution. It is important for the institution to verify the
employee before hiring and the employee management system asks the employee to enter all relevant data and
stores all required documents in the database.
b) Employee Attendance Management System: The employee attendance management system is a module
which is primarily used to record the daily attendance of the employee. The employee attendance management
system can be integrated with any smart card or fingerprint module which instantly records the presence of
the employee and updates it in the attendance system.
c) Employee Leave Management System: The employee leave management module is designed to keep a track
of the leaves an employee takes with a term or financial year. Every institute has a fixed earned leaves and sick
leaves policy and the leave management system helps in keeping a track of these leaves as when they are
exercised by the employee.
d) Employee Performance Management Software: Keeping track of the performance of an employee is of
utmost importance to any organization. The employee performance management system helps the institution
record employee performance details and analyzes their performance over a period of time.
e) Employee Payroll System: The employee payroll system has been designed to record payment and salary
details of the employee. The salary slip, provident fund details and other tax related information is recorded on
this employee payroll system for ease of access.
f) Employee Monitoring Software: Starting from attendance to leaves, all day to day information of the
employee is recorded on the employee monitoring software.
IV. SYSTEM ANALYSIS AND DESIGN
The analysis and design phase provides the developing process of employee automation system including
Software Requirement Specification (SRS) [9,10].
Figure 2: ER Diagram of the Proposed System
The SRS part to provide complete description and overview of system requirement before the developing process
is carried out. Besides that, the data flow diagram (DFD) [11] provides a view of how the system flows that able to
increase the efficiency and effectiveness to achieve system objectives. The system is designed to satisfy the user
requirements based on analysis of the system. In system design the logical model is moved to the physical aspects.
The requirements identified in the requirements analysis phase are transformed into a system design document
that accurately describes the design of the system. The database design is an important part of the software
development. The data are manipulated and stored in database and then generated output data such as listing
absent employee and count currently working employees, giving status of department, payment, promotion,
monthly attendance Report etc. The entity-relationship (ER) diagram [12] and the database schema design [12]
are shown in Figure-2 and Figure-3, respectively.](https://image.slidesharecdn.com/implementfingerprintauthenticationforemployeeautomationsystem-170924032313/85/Implement-fingerprint-authentication-for-employee-automation-system-3-320.jpg)
![International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017
Issue 09, Volume 4 (September2017) www.ijiris.com
__________________________________________________________________________________________________
IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651
Indexcopernicus: (ICV 2015): 73.48
© 2014- 17, IJIRIS- All Rights Reserved Page - 8 -
Figure 3: Database Schema Diagram of the Proposed System.
V. FINGERPRINT ENROLLMENT AND VERIFICATION
At the time of employee registration, the New Employee is asked to give their fingerprint. The finger print is taken
with fingerprint index [13], employee id, it takes three times to ensure the finger. The fingerprint scanner device
scan and generate a finger print template [14], the process in known as fingerprint enrollment (see Figure-4). The
template is stored in the database and is used for employee verification (see Figure-5). After the completing of
enrollment, employee is verified when he/she tries to enter in office. When the employee is verified, a record is
stored in database.
Figure 4: Fingerprint Enrollment Figure 5: Fingerprint Verification
VI. PROPOSED SYSTEM DESIGN
In this project work, the system is designed with three parts or panels; such Admin Panel, Operator Panel and
Employee Panel (see Figure-6). The admin has the super power of all access. The admin can edit, delete, add all
data for full system. He can check currently working employees and also who are absent till now. He can also check
the list of all employees who takes leave. The admin can manage the Designation, Department and Scales of Salary
Payment of the company. He can also give leave to a limit of date for an employee, can give promotion, can pay
employee, can generate attendance data. The admin can generate crystal report as Monthly Attendance Sheet.](https://image.slidesharecdn.com/implementfingerprintauthenticationforemployeeautomationsystem-170924032313/85/Implement-fingerprint-authentication-for-employee-automation-system-4-320.jpg)


![International Journal of Innovative Research in Information Security (IJIRIS) ISSN: 2349-7017
Issue 09, Volume 4 (September2017) www.ijiris.com
__________________________________________________________________________________________________
IJIRIS: Impact Factor Value – SJIF: Innospace, Morocco (2016): 4.651
Indexcopernicus: (ICV 2015): 73.48
© 2014- 17, IJIRIS- All Rights Reserved Page - 12 -
At any time, the home or main window connects the Finger print device, track the input fingerprint and match it to
the stored database for verification. The registration of an employe includes two forms, as shown in Figure-12 and
Figure-13. The register form takes name, father name, NID [15] etc. and store the information (see Figure-12).
After that a new finger enrollment form comes and take the finger print of the new employee. The fingerprint
register form takes three times of any one of ten fingers of an employe at a time (see Figure-14). After getting the
finger print templates it stores them to Database. The system can easily update the employee’s information and
fingerprint (see Figure-14).
VIII. CONCLUSION
Modern security is a battle between high security and low friction. Developers want users to use unique,
complicated passwords for their apps to increase security. One way to combine both performance and security is
to take advantage of fingerprint features that are now prevalent on high-end smart phones and other mobile
devices. Because, fingerprint features have a number of benefits over passwords, such as, performance, security,
permanence, etc. This is really authentic news that last couple of year many sensors device like finger print,
eye/image detection, punch card system are available in Bangladesh using this many organization secure their
system. More organizations are going to establish their business using this secure system for that they easily
maintain their employee securely. This project work is aimed to develop an Employee automation system using
fingerprint authentication. In future the system will combine with a secondary authentication scheme such as a
secure PIN, so that; it will enhance security for the application and ensure the authenticity of the user. This system
will be further developed with some additional features of original fingerprint images processing in employee
automation system.
REFERENCES
1. Grzegorz Kowalik, “Automation of Desktop Applications”, https://www.future-processing.pl/blog/automation-
of-desktop-applications/, May 2014.
2. Sonali S. Gahukar, Gargi S. Phadke, “Safeguarding Confidentiality by Fingerprint Combination”, International
Journal of Advanced Technology in Engineering and Science, Vol.4, Issue. 08, August 2016.
3. Diego Poza, “Fingerprint Authentication: High Security and Low Friction”, https://auth0.com/blog/how-
fingerprint-auth-gives-you-security/, May 2016.
4. L. O'Gorman, “Overview of Fingerprint Verification Technologies”, Elsevier Information Security Technical
Report, Vol. 3, No. 1, 1998.
5. Danny Thakkar, “Fingerprint Verification vs. Fingerprint Identification”,
http://www.touchngoid.com/fingerprint-verification-vs-fingerprint-identification/, February 2016.
6. Peck, George, “Crystal Reports 2008: The Complete Reference”, McGraw-Hill Osborne Media.Pg. 968, ISBN 0-
07-159098-6, June 2008.
7. Er.Manu Kumar Garg, Er.Harish Bansal, “Review on Fingerprint Recognition System Using Minutiae
Estimation”, International Journal of Research in Information Technology (IJRIT), Volume 1, Issue 7, July, 2013,
Pg. 74-78.
8. BioID fingerprint identification system: The next generation technology,© 2010 CareFusion Corporation or one
of its subsidiaries, carefusion.com, San Diego, CA.
9. Bourque P,Fairley R.E. (2014). “Guide to the Software Engineering Body of Knowledge (SWEBOK)”, IEEE
Computer Society. Retrieved 17 July 2014.
10.Jump up, “Software requirements specification helps to protect IT projects from failure”. Retrieved 19
December 2016.
11.Bruza, P. D., Van der Weide, Th. P., “The Semantics of Data Flow Diagrams”, University of Nijmegen, 1993.
12.Chen Peter, “The Entity-Relationship Model - Toward a Unified View of Data”, ACM Transactions on Database
Systems, Vol.1 (1): 9–36. doi:10.1145/320434.320440, March 1976.
13.Pooja A. Parmar and Sheshang D. Degadwala, “Fingerprint Indexing Approaches for Biometric Database: A
Review”, International Journal of Computer Applications, Vol.130 (13), November 2010.
14.Le Hoang Thai, Ha Nhat Tam, “Fingerprint recognition using standardized fingerprint model”, IJCSI
International Journal of Computer Science Issues, Vol.7, Issue 3, No 7, May 2010.
15.NID Services, National Identity Registration Wing, Election Commission Bangladesh.
“http://www.nidw.gov.bd/index.php?option=com_content&view=featured&Itemid=435&lang=en”.](https://image.slidesharecdn.com/implementfingerprintauthenticationforemployeeautomationsystem-170924032313/85/Implement-fingerprint-authentication-for-employee-automation-system-8-320.jpg)