intro unix/linux 03
- 1. Lesson 3-Touring Utilities and System Features
- 2. Overview Employing fundamental utilities. Linux terminal sessions. Managing input and output. Using special characters in the command-line.
- 3. Overview Managing user environment. Surveying elements of a functioning system. Creating a shell script.
- 4. Employing Fundamental Utilities Listing the contents of a directory. Counting the elements of a file. Sorting lines in a file.
- 5. Employing Fundamental Utilities Passing arguments to utilities. Creating combination files. Locating specific lines in a file.
- 6. Listing the Contents of a Directory Each utility is a tool that performs a set of very specific tasks. The “ls” utility outputs the filenames listed in the current directory. The “–F” option with ls places a forward slash at the end of the name of each directory. The “–F” option places an asterisk (*) at the end of the executable files.
- 7. Listing the Contents of the Directory The “ls –l” command displays a file’s permissions and other data about the file. The “–a” (all) option to ls includes all files in the current directory, including dot or hidden files. The “ls –alF” command displays all files with the long listing of information, and directories marked with a slash.
- 8. Counting the Elements of a File The “wc” command counts the number of lines, words, and characters in a file. It operates on the files individually. It outputs the statistics for each file and then produces a total.
- 9. Counting the Elements of a File Options for the wc command
- 10. Sorting Lines in a File The /etc/passwd (the password file) contains one line of information (a record) for each user. The “sort” utility reads the file into memory and rearranges the lines into a sorted order.
- 11. Sorting Lines in a File In the sort order, lines beginning with numbers are displayed first, lines beginning with uppercase letters second, and lines beginning with lowercase letters last. The “–r” (reverse) option is used to sort a file in reverse ASCII order.
- 12. Passing Arguments to Utilities When an argument is passed to a utility, that utility’s code determines how that argument is interpreted. Passing arguments to utilities provides an opportunity to let the shell read the base command. Passing arguments also provides the output as requested by the arguments provided to the utility.
- 13. Locating Specific Lines in a File Using the grep Utility to Locate Specific Files
- 14. Linux Terminal Sessions Starting additional Linux terminal sessions. Exiting a virtual terminal. Locating the graphical virtual terminal.
- 15. Starting Additional Linux Terminal Sessions Unix and Linux support multiple active sessions at the same time. In Linux, one monitor and keyboard can be used for multiple login sessions. The Ctrl-Alt-F2 key combination is used to open a new logon screen.
- 16. Exiting a Virtual Terminal The “exit” command can be used to end a login session in a virtual terminal environment. If multiple virtual windows are open, the execution of the exit command will only close the active virtual terminal window.
- 17. Locating the Graphical Virtual Terminal The Ctrl-Alt-F# key combination, where # is 1 through 7 or 8, is used to toggle back and forth between active sessions. The “F” keys allow a user to have both, graphical and character-based sessions, running.
- 18. Managing Input and Output Every process that is started has three defined communication locations or doors. One is its input, the second to write output, and the third to write any error messages.
- 19. Managing Input and Output The two ways to get a utility to open a file and read it are: By passing a filename as an argument to a utility. The utility locating the file and reading it.
- 20. Managing Input and Output Redirection Operators
- 21. Managing Input and Output Redirecting a file to spell’s input. Employing the input source. Creating text files with cat. Managing input and output with redirection.
- 22. Redirecting a File to spell’s Input Unix systems contain a spell check program that examines files for misspelled words. The “spell” or “ispell –l” commands can be used to examine misspelled words. All strings in a file that spell does not find on the online dictionary file are viewed as misspelled words and are displayed on the screen.
- 23. Employing the Input Source When a new process is started, the default input is the terminal keyboard. Output and error messages are initially connected to the terminal screen. The Ctrl-D key combination is used to indicate to the utility that there is no more input to the utility.
- 24. Creating Text Files with cat The “cat” command is used to create small text files without using an editor. The cat utility reads the input from the user and writes it to its output. The Ctrl-D (end-of-file, or EOF) key combination is used to tell cat that there is no additional input. By default, the keyboard is connected to the input of cat.
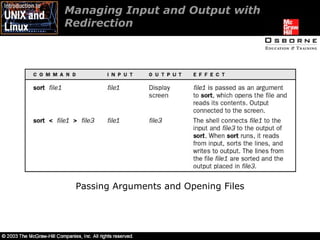
- 25. Managing Input and Output with Redirection Passing Arguments and Opening Files
- 26. Managing Input and Output with Redirection Passing Arguments and Opening Files
- 27. Using Special Characters in the Command-Line The shell interprets the > (redirect) instruction to connect the output of the previous utility to a file named right after the redirection. The | (pipe) is the instruction to connect the output of one utility to the input of another.
- 28. Using Special Characters in the Command-Line A wildcard character is a special character to the shell when specifying filenames. The shell replaces the asterisk (*) with the names of all the files in the directory and then executes the command as requested.
- 29. Using Special Characters in the Command-Line Accessing shell variables. Listing environment variables. Interpreting special characters. Creating multiple token arguments.
- 30. Using Special Characters in the Command-Line Passing complex arguments. Communicating with processes. Programming with utilities.
- 31. Accessing Shell Variables The “$” character carries a special meaning for the shell. The $ variable instructs the shell to locate the variable whose name follows, and replace the string with the variable’s value.
- 32. Listing Environment Variables When a user logs on, the shell program that interprets the commands is started. The values of several variables are given to the shell so that the computing environment is appropriate. The “evn” and the “printeven” command displays a list of the variables that are currently set for the shell. Variables and their values are essential to a functioning shell.
- 33. Listing Environment Variables The environment variables available in UNIX/Linux are: The user or USER or LOGNAME variable is the account name entered by the user while logging on to the system. The shell or SHELL variable indicates which of the shell programs is started at login. The home or HOME variable is the location of the user’s home directory. The path or PATH variable lists the directories used by shell to find UNIX utilities.
- 34. Interpreting Special Characters The characters *, !, |, >, and $ have special meaning to the shell. The shell is sometimes instructed not to interpret special characters, but to treat them as ordinary characters instead. The shell interprets enter as a special character, one that indicates the end of a command to be executed and start processing.
- 35. Interpreting Special Characters The backslash before the Enter command stops the shell from reading the enter keystroke. The backslash turns off interpretation for one character only. The interpretation for multiple characters can be turned off using single quotes. Any special characters inside single quotes are not interpreted.
- 36. Creating Multiple Token Arguments The shell interprets one or more spaces as separating the tokens on the command-line. Single quotes are used to inform the shell not to interpret the spaces.
- 37. Passing Complex Arguments The UNIX operating system provides several utilities that are used with database information. The “awk” utility is used to select and print specific fields, make calculations, and locate records by the value of specific fields.
- 38. Communicating with Processes The control character Ctrl-D is used to signal the end of file or input. The control character Ctrl-C is the interrupt signal that kills a process. The “sleep” utility allows a user to run time-consuming programs in the background. The user can continue working in the foreground on some other task after issuing the sleep command.
- 39. Communicating with Processes The ampersand (&) at the end of the sleep command tells the shell to execute the whole command line. The & instructs the shell to return a new shell prompt for the user to continue working, instead of waiting for the sleep command to finish execution.
- 40. Programming with Utilities The shell can read instructions that are placed in a file. The visual editor can be used to write the commands in a file.
- 41. The “source” command in the csh or tcsh shell can be used to instruct the current shell to read a file and execute each line in a file. The . (dot) command in the ksh, bash, or sh can be used to instruct the current shell to read a file and execute each line in a file. Programming with Utilities
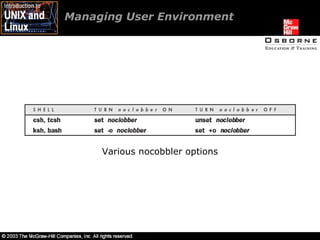
- 42. Managing User Environment Various nocobbler options
- 43. Managing User Environment To avoid accidental logouts, the user needs to instruct the shell to ignore an end-of-file character. In the csh or tcsh shells, “set ignoreeof”. In the ksh and bash shells, “set -o ignoreeof”.
- 44. Managing User Environment Various Shell Prompts
- 45. Managing User Environment In a csh or tcsh shell, the command “set prompt='myname '” is used to set the prompt. In the sh, bash, or ksh shells, the command “PS1='myname '” is used to set the prompt.
- 46. Surveying Elements of a Functioning System The variable PATH consists of a series of directories separated by a colon. The /bin directory contains some of the utilities available on the system in the form of binary files. The “which” command is used to determine the location of a utility.
- 47. Surveying Elements of a Functioning System When a user logs in to a system, the entry from either the local or the NIS network passwd file is consulted. The records in the /etc/passwd file consist of seven fields separated by colons. The “ypcat” command is used to see the passwd file information from the network server.
- 48. Surveying Elements of a Functioning System The Fields of the password File
- 49. Surveying Elements of a Functioning System The Fields of the password File
- 50. Surveying Elements of a Functioning System The “yppasswd” command is used to change a user’s password on a NIS system. The “passwd” command is used to change the user’s password on a normal system. The root user can change the user’s password to a new one without knowing the original.
- 51. Surveying Elements of a Functioning System The owner of a file determines who has permissions to read or change its contents. All files have a set of permissions that determine who can do what with the file. The minus (-) sign is used to remove any permission on the file using the chmod command. The plus (+) sign is used to add any permission on the file using the chmod command.
- 52. Creating a Shell Script The steps to create and use a shell script are: Create a file of shell commands. Make the file executable with chmod. Execute the file by entering the script name.
- 53. Creating a Shell Script Read permission is required to source a script. Execute permission is needed to start a child shell to execute its contents.
- 54. Summary Utilities are essential tools for accomplishing work in UNIX/Linux. The shell redirects input and output for processes running utilities. The shell interprets the $ as specifying a variable such as $USER and $HOME.
- 55. Summary The shell does not interpret the special meaning or special characters between single quotes. The passwd or yppasswd commands can be used to change the password. Execute permissions are needed to start a child shell to execute its contents.