Using Massively Distributed Malware in APT-Style Attacks
- 1. Using Massively Distributed Malware in APT-Style Attacks Dana Tamir IBM Trusteer Dir. Enterprise Security
- 2. © 2014 IBM Corporation IBM Security 2 2 What do you think about when you hear the term APT?
- 3. © 2014 IBM Corporation IBM Security 3 Flame Stuxnet Security Virus Trojan RAT Threat Data Credentials Malware Internet Wild Cyber WAR Discovery Alert! Breach Dangerous Detection Research $$$
- 4. © 2014 IBM Corporation IBM Security 4 Stuxnet * Designed to attack Siemens industrial systems * Caused fast- spinning centrifuges to tear themselves apart * Exploited four zero-day vulnerabilities Duqu * Looks for info to target industrial control systems * Not destructive * Uses jpeg files and encrypted dummy files as containers to exfiltrate data to C&C Gauss * A complex Cyber- espionage toolkit * Steals various kinds of data from infected machines * Includes an encrypted payload which is activated on certain specific system configs APTs => Highly Targeted Malware Flame • A sophisticated cyber-espionage malware • Infected target machines in Middle Eastern countries • Receives instructions via C&C servers
- 5. © 2014 IBM Corporation IBM Security 5 New Emerging Trend 5
- 6. © 2014 IBM Corporation IBM Security 6 Trojans Used in Financial Fraud Trojans Used in APT-Style Attacks • Targets Consumers • Used for stealing • Bank account credentials • Personal information • Sophisticated • Targets Employees • Used for stealing • Corporate credentials • Business and operational data • Sophisticated
- 7. © 2014 IBM Corporation IBM Security 7 Typical functions available with these malware families Capability Description Keylogging Captures user keystrokes and sends data to attacker Screenshot capturing record browser session, including data displayed to user Video capturing record a video stream of a browser session Form grabbing (HTTP POST grabbing) method used to capture user input from a web data form. HTML injection a method used for injecting HTML content into legitimate web pages in order to modify it. Remote execution of command line instructions enables the operator to collect data and change settings on one or more remote computers. Remote control of the infected machine allows complete control over the PC and full access to the corporate network. Evasion techniques designed to evade anti-virus and other security controls. Anti-research techniques a variety of sophisticated features designed to prevent researchers from analyzing the malware 7
- 8. © 2014 IBM Corporation IBM Security 8 Using Massive Distribution Campaigns 8 Not Targeted! Infecting Millions of Machines!
- 9. © 2014 IBM Corporation IBM Security 9 9 Massively Distributed Malware Massive Distribution Campaigns use techniques like Spear- Phishing, Drive-By Downloads, Malvertising, Watering hole attacks…
- 10. © 2014 IBM Corporation IBM Security 10 10 Massively Distributed Malware Command and Control Server Registration Configuration file
- 11. © 2014 IBM Corporation IBM Security 11 11 The Configuration Files • Provided by the Command and Control Server • Contain operational information, like: • Targets and Operational Triggers • Information requested • Alternative Command and Controls • Can be Updated! • New operational triggers and targets • New information requested • Alternative Command and Controls • Software upgrades
- 12. Examples?
- 13. © 2014 IBM Corporation IBM Security 13 Example: The Citadel Trojan 13 Citadel Configuration File
- 14. © 2014 IBM Corporation IBM Security 14 Available for sale on the Russian Underground New version offers “classic” Zeus and new capabilities Enables the attacker to run shell commands off the infected device Can map the network on which the infected device is Obviously not added for financial fraud… Built-in VNC (the VNCfox) is a valuable tool “Crowd-sourcing” Will not work on devices that use a Cyrillic keyboard layout (do not wish to target Russian or Ukrainian systems) 14
- 15. © 2014 IBM Corporation IBM Security 15 Constantly under development 15 Malware
- 16. © 2014 IBM Corporation IBM Security 16
- 17. © 2014 IBM Corporation IBM Security 17 From The Citadel Configuration File Instructed to look for user access to certain URL addresses Form Grabbing/ “HTTP POST”: grab all the information submitted by the user The relevant section from the configuration file (shown in a Trusteer proprietary format) 17
- 18. © 2014 IBM Corporation IBM Security 18 Grabbing webmail login credentials http://mail.target-company.com/* 18
- 19. © 2014 IBM Corporation IBM Security 19 19
- 20. © 2014 IBM Corporation IBM Security 20 Citadel triggered by specific processes Citadel instructed to start keylogging (capturing user keystrokes) when specific processes are running. The relevant part of the configuration is shown below (in IBM Trusteer’s proprietary format): 20
- 21. © 2014 IBM Corporation IBM Security 21 Examples of Citadel Evasion Techniques Designed to evade anti-virus and other traditional security controls Anti-research techniques: won’t execute if env settings are set to ‘debug’ mode Using “AutoCMD” functionality (run shell commands on infected device): – The variant creates a new user on the infected device – New user added to native windows remote desktop protocol (RDP) group. – So, if the malware is removed from the infected device, the operator still has a backdoor into it using Windows RDP. 21
- 22. © 2014 IBM Corporation IBM Security 22 AlienSpy RAT used to deliver the popular Citadel Trojan Similar to other RATs, AlienSpy RAT provides the attacker with full control over the compromised system. Network traffic encryption is performed to obfuscate the malicious network traffic with the command and control server (CnC) AlienSpy receives commands to download and execute a file in the victim system – At least one variant received commands to infect the victim system with Citadel C&C AlienSpy (PayslipDetails.jar) Citadel C&C Dropper
- 23. © 2014 IBM Corporation IBM Security 23 Using Trojans to Massively Distribute Trojans …so far managed to infect over 770,000 machines around the world. …designed primarily to disseminate other kinds of malware and has been operating since at least 2012 somewhat under the radar of researchers…
- 24. © 2014 IBM Corporation IBM Security 24 The Dyre Trojan First appeared in June 2014 Distributed through massive spear-phishing campaigns Initially targeted customers of large financial institutions Targets include: Bank of America, Citigroup, and Royal Bank of Scotland Group Plc, and JP Morgan Chase customers. Undergone many changes in a very short period Uses some noteworthy propagation and evasion techniques. 24
- 25. © 2014 IBM Corporation IBM Security 25 The target is business data!
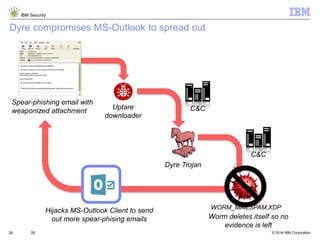
- 26. © 2014 IBM Corporation IBM Security 26 Dyre compromises MS-Outlook to spread out 26 Spear-phishing email with weaponized attachment Uptare downloader C&C Dyre Trojan C&C WORM_MAILSPAM.XDP Hijacks MS-Outlook Client to send out more spear-phising emails Worm deletes itself so no evidence is left
- 27. © 2014 IBM Corporation IBM Security 27 Dyre Evasion Techniques Fast evolution: a new binary code version can be released every three days. Uses Secure Socket Layers (SSL) to protect C&C communications Has a mechanism that enables the Trojan to find an alternate C&C (in case the hard coded C&Cs aren’t available) – Uses a domain generation algorithm (DGA) to generate URLs on various top- level domains (cc, ws, to, in, hk, cn, tk, and so) – Similar to the mechanism used by Downad/Conficker malware. 27
- 28. © 2014 IBM Corporation IBM Security 28 The Latest News on Dyre: Dyre Wolf
- 29. © 2014 IBM Corporation IBM Security 29 The Carbanak attack 29
- 30. © 2014 IBM Corporation IBM Security 30 The Carbanak Malware Distributed through drive-by downloads and spear-phishing Designed for espionage, data exfiltration and providing remote access Once the system is infected, Carbanak logs keystrokes and takes screenshots every 20 seconds (intercepts ResumeThread call) Can install additional malware like the Ammyy RAT 30
- 31. © 2014 IBM Corporation IBM Security 31 Carbanak Evasion Techniques Carbanak copies itself into “%system32%com” with the name “svchost.exe” and then deletes the original exploit payload Carbanak injects its code into svchost.exe. Most of the actions described below happen within this process. To communicate with the C&C it uses the HTTP protocol with RC2+Base64 encryption, adding characters not included in Base64. Latest Carbanak samples are digitally signed (seem trusted)
- 32. © 2014 IBM Corporation IBM Security 32 Characteristics of Massively Distributed APT malware 32
- 33. © 2014 IBM Corporation IBM Security 33 1:500 PCs infected with MAD APT malware 33
- 34. © 2014 IBM Corporation IBM Security 34 Recommendations Traditional security controls aren’t effective • > New approach needed! There is no silver bullet! Multi-layered protection required – Employee Endpoints – Servers – Networks Security Intelligence Emergency Response Services 34
- 35. © 2014 IBM Corporation IBM Security 35 IBM is uniquely positioned to offer integrated protection 35 A dynamic, integrated system to disrupt the lifecycle of advanced attacks and prevent loss Open Integrations Global Threat Intelligence Ready for IBM Security Intelligence Ecosystem IBM Security Network Protection XGS Smarter Prevention Security Intelligence IBM Emergency Response Services Continuous Response IBM X-Force Threat Intelligence • Leverage threat intelligence from multiple expert sources • Prevent malware installation and disrupt malware communications • Prevent remote network exploits and limit the use of risky web applications • Discover and prioritize vulnerabilities • Correlate enterprise-wide threats and detect suspicious behavior • Retrace full attack activity, Search for breach indicators and guide defense hardening • Assess impact and plan strategically and leverage experts to analyze data and contain threats • Share security context across multiple products • 100+ vendors, 400+ products Trusteer Apex Endpoint Malware Protection IBM Security QRadar Security Intelligence IBM Security QRadar Incident Forensics IBM Guardium Data Activity Monitoring • Prevent remote network exploits and limit the use of risky web applications IBM Endpoint Manager • Automate and manage continuous security configuration policy compliance
- 36. © 2014 IBM Corporation IBM Security 36 Trusteer Apex Advanced Malware Protection Multi-layered protection against advanced malware and credentials theft 36 Threat and Risk Reporting Vulnerability Mapping and Critical Event Reporting Advanced Threat Analysis and Turnkey Service Credential Protection Exploit Chain Disruption Advanced Malware Detection and Mitigation Malicious Communication Prevention Lockdown for Java Global Threat Research and Intelligence Global threat intelligence delivered in near-real time from the cloud • Alert and prevent phishing and reuse on non- corporate sites • Prevent infections via exploits • Zero-day defense by controlling exploit-chain choke point • Mitigates mass- distributed advanced malware infections • Cloud based file inspection for legacy threats • Block malware communication • Disrupt C&C control • Prevent data exfiltration • Prevent high-risk actions by malicious Java applications
- 37. © 2014 IBM Corporation IBM Security 37 37 No.ofTypes Attack Progression Data exfiltrationExploit Delivery of weaponized content Exploitation of app vulnerability Malware delivery Malware persistency Execution and malicious access to content Establish communication channels Data exfiltration Breaking the Threat LifeCycle Pre-exploit 0011100101 1101000010 1111000110 0011001101 Strategic Chokepoint Strategic Chokepoint Strategic Chokepoint Advanced Malware Prevention Endpoint Vulnerability Reporting Credential Protection Destinations (C&C traffic detection) Endless Unpatched and zero-day vulnerabilities (patching) Many Weaponized content (IPS, sandbox) Endless Malicious files (antivirus, whitelisting) Endless Many Malicious behavior activities (HIPs) Exploit Chain Disruption Lockdown for Java Malicious Communication Blocking
- 38. © 2013 IBM Corporation IBM Security Systems 38 www.ibm.com/security © Copyright IBM Corporation 2014. All rights reserved. The information contained in these materials is provided for informational purposes only, and is provided AS IS without warranty of any kind, express or implied. IBM shall not be responsible for any damages arising out of the use of, or otherwise related to, these materials. Nothing contained in these materials is intended to, nor shall have the effect of, creating any warranties or representations from IBM or its suppliers or licensors, or altering the terms and conditions of the applicable license agreement governing the use of IBM software. References in these materials to IBM products, programs, or services do not imply that they will be available in all countries in which IBM operates. Product release dates and/or capabilities referenced in these materials may change at any time at IBM’s sole discretion based on market opportunities or other factors, and are not intended to be a commitment to future product or feature availability in any way. IBM, the IBM logo, and other IBM products and services are trademarks of the International Business Machines Corporation, in the United States, other countries or both. Other company, product, or service names may be trademarks or service marks of others. Statement of Good Security Practices: IT system security involves protecting systems and information through prevention, detection and response to improper access from within and outside your enterprise. Improper access can result in information being altered, destroyed or misappropriated or can result in damage to or misuse of your systems, including to attack others. No IT system or product should be considered completely secure and no single product or security measure can be completely effective in preventing improper access. IBM systems and products are designed to be part of a comprehensive security approach, which will necessarily involve additional operational procedures, and may require other systems, products or services to be most effective. IBM DOES NOT WARRANT THAT SYSTEMS AND PRODUCTS ARE IMMUNE FROM THE MALICIOUS OR ILLEGAL CONDUCT OF ANY PARTY.