Mitigating Exploits Using Apple's Endpoint Security
- 1. Mitigating exploits using Apple's Endpoint Security Csaba Fitzl Twitter: @theevilbit
- 2. whoami • author of "macOS Control Bypasses" @ Offensive Security • ex red/blue teamer • macOS researcher • husband, father • hiking 🥾 🏔 • yoga 🧘
- 3. agenda 1. process injection attacks 2. symlink attacks 3. Endpoint Security framework 4. developing the app 5. the app's logic 6. demos
- 5. why important? • process injection is a big ⛔ on macOS • access to process's privileges • TCC • keychain • impersonate XPC client (XPC LPEs) • impersonate KEXT client
- 6. DYLD_INSERT_LIBRARIES • classic • SIP kills it (hardened runtime, platform binaries) • still can enable it with entitlement -> if possible don't 🙏
- 7. DYLIB hijacking and proxying • discussed in detail by Patrick Wardle in 2015 • plant a dylib the app looks for, or replace one with your own • SIP / library validation kills it • still can enable it with entitlement -> NOOOO!!!! • problem: app needs to support 3rd party plugins => bypass TCC (Apple & 3rd parties)
- 8. task for pid • inject by getting the task port • ⚠ debug builds with bad entitlement ⚠ • SIP kills this • notarization checks for `com.apple.security.get-task-allow`
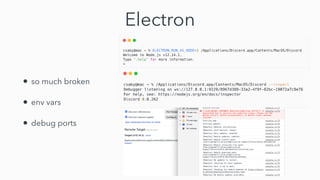
- 9. Electron • so much broken • env vars • debug ports
- 10. vulnerabilities • CVE-2020-26893 - ClamXAV AntiVirus XPC LPE • CVE-2020-29621 - coreaudiod TCC bypass • CVE-2020-25736 - Acronis True Image 2021 XPC LPE • CVE-2020-24259 - Signal macOS TCC bypass • CVE-2020-14978 - F-Secure XPC • ...
- 11. symlink attacks
- 12. the approach • process running as root writes or modi fi es fi les at a user controllable location • place a symlink or hardlink, pointing to a root accessible location
- 13. vulnerabilities • CVE-2020-9900 - Crash Reporter LPE • CVE-2021-1786 - Crash Reporter arbitrary fi le deletion • CVE-2020-3855 - macOS DiagnosticMessages arbitrary fi le overwrite • CVE-2020-3762 - Adobe installer LPE • ...
- 14. MACF - Mandatory Access Control Framework
- 15. MACF • origin: TrustedBSD MAC • implemented in kernel • policy modules extend the kernel • can place hooks in supported location • very powerful
- 16. MACF • very - very powerful • was part of KDK till OS X 10.12 (never of fi cially supported) • mac.h header was removed • available in xnu: `security/mac.h`, `security/mac_framework.h` • examples: AppleMobileFileIntegrity, Sandbox, EndpointSecurity, Quarantine (=Gatekeeper)
- 17. MACF • typical callout from xnu: mac_......
- 18. MACF
- 19. MACF • MAC_CHECK • iterates over all policy frameworks • mpo_... (mac_policy.h)
- 21. ES • KEXT - MACF, kauth • dylib - C API for clients • endpointsecurityd - loading SEXT via launchd • sysextd - validation and copy • SystemExtension.framework - activation and deactivation of the extension • systemextensionsctl - basic control of sysxextd • more: Scott Knight's OBTS talk 1: Scott Knight, https://knight.sc/reverse%20engineering/2019/10/31/macos-catalina-privilege-escalation.html
- 22. ES • MACF policy (EndpointSecurity) • ~60 hooks
- 23. ES • user mode events are mapped to kernel MACF hooks • examples: • ES_EVENT_TYPE_NOTIFY_CHROOT - es_vnode_check_chroot • ES_EVENT_TYPE_NOTIFY_MOUNT - es_mount_check_mount_late • ES_EVENT_TYPE_NOTIFY_MMAP - es_ fi le_check_mmap • ES_EVENT_TYPE_AUTH_GET_TASK - es_proc_check_get_task
- 24. ES • very powerful!!! • extending MACF to user mode • MACF was never of fi cially supported • now we have in user mode ❤
- 26. requirements • entitlement: com.apple.developer.endpoint-security.client • Apple's good will
- 27. getting entitled • 2020 March - requested ES entitlement • 2020 April - got developer version • 2020 - emails going to "black hole" at Apple • ... • 2021 January - got the entitlement • frustration, demotivation, annoyed, extremely bad experience - luckily I don't do this for living
- 28. sources • used Patrick Wardle's ProcessMonitor and FileMonitor • also reviewed Stephen Davis’s Crescendo
- 29. es_client
- 30. the logic
- 31. ES_EVENT_TYPE_AUTH_EXEC • checks: • argument • --inspect, --inspect-brk, --remote-debugging-port • environment variables • DYLD_INSERT_LIBRARIES • CFNETWORK_LIBRARY_PATH • RAWCAMERA_BUNDLE_PATH • ELECTRON_RUN_AS_NODE
- 33. ES_EVENT_TYPE_AUTH_MMAP • dylib injection protection • "enforce" library validation • slow - disk I/O
- 34. ES_EVENT_TYPE_AUTH_LINK • event for hardlinks • low privilege process isn't allowed to point to high privilege location
- 35. ES_EVENT_TYPE_NOTIFY_CREATE • track symbolic links • low privilege process isn't allowed to point to high privilege location • detect only - don't know the target before creation
- 36. demo - w/o Shield CVE-2020-26893 - ClamXAV AntiVirus XPC LPE
- 37. demo
- 38. demo - w/ Shield CVE-2020-26893 - ClamXAV AntiVirus XPC LPE
- 40. wrap up • injection and fi le link attacks responsible for many logic bugs • ES framework is based on MACF • ES extends MACF to user mode, very powerful • can be used to detect and block logic attacks • it's a pain to get the ES entitlement
- 42. Further resources • Wojciech Reguła ( @_r3ggi ): Abusing and Securing XPC in macOS Apps Objective by the Sea v3 • Julia Vashchenko ( @iaronskaya ): Job(s) Bless Us! Privileged Operations on macOS Objective by the Sea v3 • Tyler Bohan ( @1blankwall1 ): OSX XPC Revisited - 3rd Party Application Flaws OffensiveCon 19 • Ian Beer ( @i41nbeer ): A deep-dive into the many fl avors of IPC available on OS X Jailbreak Security Summit 2015
- 43. Links • http://www.trustedbsd.org/mac.html • https://blog.xpnsec.com/macos-injection-via-third-party-frameworks/ • https://www.offensive-security.com/offsec/am fi -syscall/ • https://www.semanticscholar.org/paper/New-approaches-to-operating-system-security-Watson/ f89682c6cf943ce349031270e685ee2dddee9376 • https://knight.sc/reverse%20engineering/2019/08/24/system-extension-internals.html • http://newosxbook.com/articles/eps.html • https://github.com/xorrior/goesf/blob/master/appmon.m • https://github.com/theevilbit/Shield