Operating System Security in the Cloud
- 1. Michigan Oracle Users Summit October 25, 2023 8:30am EST W210C (4) Operating System Security in the Cloud
- 2. Slide 2 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech INTRODUCTION
- 3. Slide 3 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech About Me Ahmed Aboulnaga • Master’s degree in Computer Science from George Mason University • Recent emphasis on cloud, DevOps, middleware, security in current projects • Oracle ACE Pro, OCE, OCA • Author, Blogger, Presenter • @Ahmed_Aboulnaga
- 4. Slide 4 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech 2015 5.6 million fingerprints stolen in cyberattack from OPM due to hacks 2019 530 million users had their personal data stolen from Facebook and posted to a public database, including phone numbers, full names, locations, some email addresses, and other profile details 2019 1.1 billion user’s data exposed over 8 months at Alibaba as user information was secretly scraped 2021 LinkedIn fell victim to a data scraping breach affecting 700 million LinkedIn profiles, and data posted on the dark web, including email addresses, phone numbers, location, gender, and other details 2021 Accenture was hit by hackers connected to the LockBit ransomware group, with proprietary corporate data as well as customer’s system stolen and leaked 2023 260,000 customers’ data at Toyota Motor Corporation was exposed online due to a misconfigured cloud environment https://www.arcserve.com/blog/7-most-infamous-cloud-security-breaches Why This Presentation?
- 5. Slide 5 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Cloud Assets are the Biggest Targets for Cyberattacks Businesses that experienced a data breach in their cloud environment last year (up 4% from previous year) Amount of sensitive data stored in the cloud for 75% of business (up 26% from previous year) Sensitive data that is encrypted in the cloud Operating systems provisioned in the cloud is Linux 5 https://cpl.thalesgroup.com/about-us/newsroom/2023-cloud-security-cyberattacks-data-breaches-press-release 39% 40% 45% 90%
- 6. Slide 6 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech My Servers Were Hacked in 2016 • Suspicious files/services manually identified • Publicly exposed servers are biggest risk 6
- 7. Slide 7 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Explaining Vulnerabilities
- 8. Slide 8 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech CVE • CVE stands for Common Vulnerabilities and Exposures • MITRE is a nonprofit that operates research and development centers sponsored by the federal government • Identifies and catalogs publicly disclosed cybersecurity vulnerabilities and exposures in software or firmware into a free “dictionary” • Each CVE contains an identification number, a description, and at least one public reference • CVE entries are used in numerous cybersecurity tools ▪ Launched in 1999 ▪ Operated by MITRE ▪ Available at cve.mitre.org ▪ Freely accessible ▪ Lists publicly disclosed cybersecurity vulnerabilities
- 9. Slide 9 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech CVE What is a vulnerability? • A mistake in software code that provides an attacker with direct access to a system or network. It could allow an attacker to pose as a super- user or system administrator with full access privileges. What is an exposure? • A system configuration issue or a mistake in software that allows access to information or capabilities that can be used by a hacker as a stepping-stone into a system or network.
- 10. Slide 10 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Example of a CVE 10 https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-1872
- 11. Slide 11 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Example of a CVE 11 https://nvd.nist.gov/vuln/detail/CVE-2023-1872
- 12. Slide 12 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Enter OCI Security Services When to Use OS Management Service (OSMS) An OCI service to monitor and manage patches to select Linux and Windows compute operating systems For patch automation of single or group of servers Oracle Ksplice A feature in Oracle Linux that supports the immediate and non-disruptive patching of the Oracle Linux operating system with zero downtime and no reboots For zero downtime patching (e.g., Linux kernel upgrade) Oracle Autonomous Linux An OCI managed service that monitors for critical events and performs automatic daily updates of Linux operating systems, taking advantage of Oracle Ksplice to offload operating system management duties from your administrators For automated daily patching (including kernel and security patches) Vulnerability Scanning Service (VSS) A free OCI service that checks hosts and containers for vulnerabilities Vulnerability scanning
- 13. Slide 13 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech OS Management Service
- 14. Slide 14 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech OS Management Service (OSMS) • Manages and monitors upgrades and patches on the operating systems of your compute instances • From a central console, out-of-date operating system packages are identified by the services and can easily be updated (or scheduled) across a group of instances • Documentation: https://docs.oracle.com/en-us/iaas/os-management/home.htm • Can manage both Linux packages and Windows updates • Compute instances can be grouped together in managed instance groups, allowing for updates to be scheduled and pushed to the entire group
- 15. Slide 15 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech OSMS Prerequisites • Use a supported image – Supported Linux images include Oracle Linux 6, 7, 8, and 9 or later, as well as Oracle Autonomous Linux – Supported Windows images include Windows Server 2012 R2 Standard, 2026 Standard, and 2019 Standard • Create a dynamic group to include the OCID of the compute instances to manage (e.g., a condition in a rule statement). • Create an IAM policy to allow instances to use OSMS • For Windows, define a security list to allow access to the Windows update server • Attach the compute instances to a VCN with a private subnet with a NAT gateway or public subnet with an internet gateway (other conditions exist and documented in the OCI documentation) • Ensure that the Oracle Cloud Agent is installed and running on the compute instances • Ensure that the OS Management Service Agent plugin is enabled and running on the Oracle Cloud Agent • OSMS relies on the OS Management Service Agent plugin
- 16. Slide 16 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech OSMS Prerequisites • All Oracle Linux 8+ images in OCI now include both the Oracle Cloud Agent and the OS Management Service Agent plugin enabled by default, so nothing needs to be done for newly created compute instances
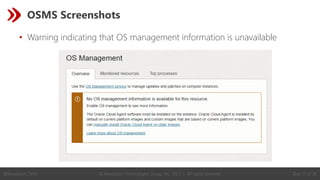
- 17. Slide 17 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech OSMS Screenshots • Warning indicating that OS management information is unavailable
- 18. Slide 18 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech OSMS Screenshots • Verifying OS Management on a compute instance
- 19. Slide 19 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Updating Packages on a Compute Instance 1. Navigate to your compute instance and click on OS Management 2. In the Overview tab, click on the 3 dots to the right 3. One option includes clicking on Install security updates to automatically install all relevant operating system security packages, alternatively, click on View OS Management details 4. On this page, the Available Package Updates page, a list of available packages to be updated is provided. Packages that are associated with a CVE are listed and can be patched manually and immediately 5. Select the packages to update and click on Install Updates
- 20. Slide 20 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Oracle Ksplice
- 21. Slide 21 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Oracle Ksplice • Most Linux kernel upgrades and security patches require a system reboot • It often requires coordination and planning, and upgrades and patching are disruptive in nature • Ksplice is an open-source extension to the Linux kernel • Allows for kernel upgrades and security patches to be applied without the need of a reboot • Created in 2009 by Ksplice, Inc., and later acquired by Oracle in 2011 • Additional background and information can be found at https://ksplice.oracle.com
- 22. Slide 22 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Ksplice Prerequisites • The host must be set up as an Oracle Ksplice client • The host must be connected to the Internet • The host must be registered with the Unbreakable Linux Network if Ksplice is configured in online mode – Online mode allows Ksplice to apply updates automatically – Requires access to and register with the Unbreakable Linux Network through the Internet • Oracle Ksplice can run on any Oracle Linux system, including on-premises hosts • Automatically installed on all compute instances created in OCI and does not need to be registered with the Unbreakable Linux Network
- 23. Slide 23 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Ksplice Commands # List available kernel updates only ksplice kernel show --available ksplice -n kernel upgrade # Apply available kernel updates only ksplice -y kernel upgrade # Remove all applied patches ksplice user remove --all # Disable automatic updates touch /etc/uptrack/disable # Enable automatic updates rm /etc/uptrack/disable # View the help page man ksplice # View the summarized help page ksplice –help # List patches that have been applied ksplice all show # List all available updates ksplice all show --available ksplice -n all upgrade # Apply all available updates ksplice -y all upgrade
- 24. Slide 24 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Oracle Autonomous Linux
- 25. Slide 25 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Oracle Autonomous Linux • Autonomous Linux is a service that manages a Linux compute instance – Must first create the compute instances as you normally would using the Oracle Autonomous Image – Autonomous Linux leverage OSMS which in turn relies on two plugins: the Oracle OS Management Service Agent plugin and Autonomous Linux plugin • Autonomous Linux provides some key capabilities that include: – Automatic updates – Automatic daily updates to Linux compute instances, including zero- downtime Ksplice updates – Event monitoring – Instance monitoring by capturing events that can be viewed in the console, CLI, or API – Notifications – Notifications on updates and events
- 26. Slide 26 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Oracle Autonomous Image
- 27. Slide 27 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Oracle Autonomous Linux • No cost to using the Oracle Autonomous Linux image • Monitoring, management, and maintenance of Linux packages and kernel updates are offloaded to the Oracle Autonomous Linux service • Package maintenance is effectively surrendered to the service • Not a fully managed service though – Root access is still available and all administrative privileges also remain available to the system administrator
- 28. Slide 28 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Oracle Autonomous Linux Prerequisites • Appropriate IAM policies • Required agent (Oracle Cloud Agent) • Required plugins (OS Management Service Agent and Oracle Autonomous Linux plugins) • Must use of the August 2021 Oracle Autonomous Linux image or later • Free tier and custom images are not supported
- 29. Slide 29 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Oracle Autonomous Linux In Action
- 30. Slide 30 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Vulnerability Management Service
- 31. Slide 31 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Vulnerability Scanning Service (VSS) • Free host scanning service exclusive to OCI • Periodically scans compute instances and in search for CVEs in the file system • Reports on the security risk and identifies if patching is required • Can scan for vulnerabilities in compute instances and container registry images
- 32. Slide 32 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Vulnerability Scanning Agent
- 33. Slide 33 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Final Thoughts
- 34. Slide 34 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Final Thoughts • Benefits of OSMS, Ksplice, Autonomous Linux, and VSS are to ensure a strong security posture of your operating system • Benefits: – Maintain a high security and compliance posture – One way to outpace cybersecurity threats is by frequently applying patch and kernel updates, as well as continuing to scan for vulnerabilities – Improve availability – This is through the use of zero-downtime services such as Ksplice – Reduce operational costs – Scheduling and applying updates across an entire group of instances and leveraging managed services for kernel or patch updates all provide the ability to optimize operations while scaling your infrastructure, using OSMS and Autonomous Linux • Very good options for small and mid-size companies that have insufficient administrator staff and less stringent promotion processes, at the expense of control for services such as Autonomous Linux
- 35. Slide 35 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech Demo
- 36. Slide 36 of 36 © Revelation Technologies Group, Inc. 2023 | All rights reserved. @Revelation_Tech