Palo Alto Networks Application Usage and Risk Report - Key Findings for Hong Kong
- 1. Five Facts About Application Usage on Enterprise Networks in Hong Kong Application Usage and Risk Report December 2011
- 3. Average number of social networking applications per organization? A total of 63 different social networking applications were found in 98% of the 46 participating organizations with an average of 14 found on each network.
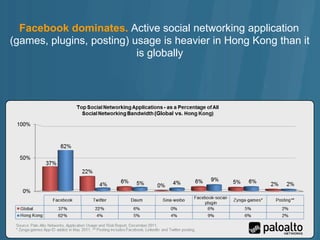
- 5. Which application is used more heavily? Based on the percentage of social networking bandwidth consumed, Daum consumed 5% while Twitter consumed 4%. Facebook consumed a staggering 62% of the social networking bandwidth.
- 6. Facebook dominates. Active social networking application (games, plugins, posting) usage is heavier in Hong Kong than it is globally
- 8. Average number of browser-based filesharing applications per organization? A total of 41 different browser-based filesharing applications were found in 100% of the 46 participating organizations with an average of 12 in each.
- 9. Browser-based filesharing use cases: work or entertainment. Both uses have a common set of business and security risks that organizations must address.
- 11. The number of applications using Port 80 (tcp/80) only? The number of applications that ONLY use Port 80 is 204 or 28% of the 734 applications found in the participating organizations.
- 13. Percentage of total bandwidth consumed by applications not using tcp/80? Only 19% of the total bandwidth is being consumed by 195 (27% of 734) applications that DO NOT USE port 80 at all. Ever.
- 14. Port 80 only security is shortsighted. The common perception is that Port 80 (tcp/80) is where all the traffic and all the problems are. A port 80 emphasis is an absolute requirement; but too much focus is shortsighted.
- 16. Palo Alto Networks Application Usage and Risk Report www.paloaltonetworks.com/aur