Patch Tuesday Analysis - December 2015
- 1. Chris Goettl Sr. Product Manager Minimizing the Impact of Patch Tuesday Wednesday, December 9th, 2015 Dial In: 1-855-749-4750 (US) Attendees: 922 990 888
- 2. Shavlik Confidential Feel free to ask questions via the online Q&A link in the WebEx interface. Questions may be answered during the presentation. Unanswered questions will be resolved via email after the presentation is over. A copy of this presentation will be available at http://www.shavlik.com/webinars/ after the webinar. 2 Logistics
- 3. Shavlik Confidential December 2015 Patch Tuesday Overview Review December 2015 Security Bulletins Patch Recommendations Other patches released since last Patch Tuesday 3 Agenda
- 5. Shavlik Confidential 12 Microsoft Security Bulletins / 71 Vulnerabilities Addressed Adobe Flash Player Bulletin / 78 Vulnerabilities Addressed Google Chrome Release / 7+ Vulnerability Addressed + 78 from Flash Player Plug-In Affected Products: All supported Windows operating systems Internet Explorer, Edge Microsoft Office 2010, 2013 .Net Framework Microsoft Lync Skype for Business Silverlight Adobe Flash Player Google Chrome 5 Patch Tuesday Overview for December 2015
- 6. Shavlik Confidential Security Bulletins: 8 bulletin is rated as Critical. 4 bulletins are rated as Important. Vulnerability Impact: 10 bulletins address vulnerabilities that could allow Remote Code Execution. 2 bulletins address vulnerabilities that could allow Elevation of Privileges. 6 Overview for Microsoft December 2015
- 7. Shavlik Confidential Security Bulletins: Adobe Flash Player (Priority 1) Google Chrome (High) Vulnerability Impact: Adobe Flash Player addresses vulnerabilities that could allow Code Execution and Security Feature Bypass. Google Chrome addresses a vulnerability that could allow type confusion, use-after-free, escaping issues and allows the Flash Player Plug-In update resolving the additional Flash vulnerabilities. 7 Overview for 3rd Party Vendors December 2015
- 8. Shavlik Confidential • From a bulletin perspective, many of the updates this month overlap. Some bulletins may also apply to the same machine multiple times for different affected products. • Adobe Flash Player distribution changes coming January 22nd, 2016. • Internet Explorer changes coming January 12th, 2016. 8 Known Issues Things to watch out for
- 9. Shavlik Confidential Maximum Severity: Critical Affected Products: Windows 10, Edge, Internet Explorer, .Net Framework Description: This update for Windows 10 includes functionality improvements and resolves the vulnerabilities in Windows that are described in the following Microsoft security bulletins and advisory: 3119075 MS15-135, 3116130 MS15-133, 3116162 MS15-132, 3104503 MS15-128, 3116178 MS15-126, 3116184 MS15-125, 3116180 MS15-124. Impact: Remote Code Execution, Elevation of Privilege Fixes 58 vulnerabilities: CVE-2015-6083, CVE-2015-6134, CVE-2015-6135, CVE-2015-6136, CVE-2015-6138, CVE-2015-6139, CVE-2015-6140, CVE-2015- 6141, CVE-2015-6142, CVE-2015-6143, CVE-2015-6144, CVE-2015-6145, CVE-2015-6146, CVE-2015-6147, CVE-2015-6148, CVE- 2015-6149, CVE-2015-6150, CVE-2015-6151, CVE-2015-6152, CVE-2015-6153, CVE-2015-6154, CVE-2015-6155, CVE-2015-6156, CVE-2015-6157, CVE-2015-6158, CVE-2015-6159, CVE-2015-6160, CVE-2015-6161, CVE-2015-6162, CVE-2015-6164, CVE-2015- 6139, CVE-2015-6140, CVE-2015-6142, CVE-2015-6148, CVE-2015-6151, CVE-2015-6153, CVE-2015-6154, CVE-2015-6155, CVE- 2015-6158, CVE-2015-6159, CVE-2015-6161, CVE-2015-6168, CVE-2015-6169, CVE-2015-6170, CVE-2015-6176, CVE-2015-6135, CVE-2015-6136, CVE-2015-6106, CVE-2015-6107, CVE-2015-6108, CVE-2015-6128, CVE-2015-6132, CVE-2015-6133, CVE-2015- 6126, CVE-2015-6171, CVE-2015-6173, CVE-2015-6174, CVE-2015-6175 (Publicly Disclosed, Exploited in Wild) Replaces: CSWU-015 Restart Required: Requires Restart 9 CSWU-016: Cumulative update for Windows 10: December 8, 2015
- 10. Shavlik Confidential Maximum Severity: Critical Affected Products: Internet Explorer Description: This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights. Impact: Remote Code Execution Fixes 30 vulnerabilities: CVE-2015-6083, CVE-2015-6134, CVE-2015-6135, , CVE-2015-6136, CVE-2015-6138, CVE-2015-6139, CVE- 2015-6140, , VE-2015-6141, CVE-2015-6142, CVE-2015-6143, CVE-2015-6144, CVE-2015-6145, CVE-2015- 6146, CVE-2015-6147, CVE-2015-6148, CVE-2015-6149, CVE-2015-6150, CVE-2015-6151, CVE-2015-6152, CVE-2015-6153, CVE-2015-6154, CVE-2015-6155, , CVE-2015-6156, CVE-2015-6157, CVE-2015-6158, CVE- 2015-6159, CVE-2015-6160, CVE-2015-6161, CVE-2015-6162, CVE-2015-6164 Replaces: 3100773 in MS15-112, 3105213 in MS15-112, 3105211 in MS15-112 Restart Required: Requires Restart 10 MS15-124: Cumulative Security Update for Internet Explorer (3116180)
- 11. Shavlik Confidential Maximum Severity: Critical Affected Products: Windows, Edge Description: This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights. Impact: Remote Code Execution Fixes 15 vulnerabilities: CVE-2015-6139, CVE-2015-6140, CVE-2015-6142, CVE-2015-6148, CVE-2015-6151, CVE-2015-6153, CVE- 2015-6154, CVE-2015-6155, CVE-2015-6158, CVE-2015-6159, CVE-2015-6161, CVE-2015-6168, CVE-2015- 6169, CVE-2015-6170, CVE-2015-6176 Replaces: 3105213 in MS15-113, 3105211 in MS15-113 Restart Required: Requires Restart 11 MS15-125: Cumulative Security Update for Microsoft Edge (3116184)
- 12. Shavlik Confidential Maximum Severity: Critical Affected Products: Windows Description: This security update resolves vulnerabilities in the VBScript scripting engine in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if an attacker hosts a specially crafted website that is designed to exploit the vulnerabilities through Internet Explorer (or leverages a compromised website or a website that accepts or hosts user-provided content or advertisements) and then convinces a user to view the website. An attacker could also embed an ActiveX control marked "safe for initialization" in an application or Microsoft Office document that uses the Internet Explorer rendering engine to direct the user to the specially crafted website. Impact: Remote Code Execution Fixes 2 vulnerabilities: CVE-2015-6135, CVE-2015-6136 Replaces: 3068368 in MS15-066, Restart Required: May Require Restart 12 MS15-126: Cumulative Security Update for JScript and VBScript to Address Remote Code Execution (3116178)
- 13. Shavlik Confidential Maximum Severity: Critical Affected Products: Windows Description: This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker sends specially crafted requests to a DNS server. Impact: Remote Code Execution Fixes 1 vulnerabilities: CVE-2015-6125 Replaces: 2647170 in MS12-017, Restart Required: Requires Restart 13 MS15-127: Security Update for Microsoft Windows DNS to Address Remote Code Execution (3100465)
- 14. Shavlik Confidential Maximum Severity: Critical Affected Products: Windows, Office, .Net Framework, Lync, Skype, Silverlight Description: This security update resolves vulnerabilities in Microsoft Windows, .NET Framework, Microsoft Office, Skype for Business, Microsoft Lync, and Silverlight. The vulnerabilities could allow remote code execution if a user opens a specially crafted document or visits a webpage that contains specially crafted embedded fonts.. Impact: Remote Code Execution Fixes 3 vulnerabilities: CVE-2015-6106, CVE-2015-6107, CVE-2015-6108 Replaces: 3097877 in MS15-115, 3085529 in MS15-097, 3072303 in MS15-080, 3048068 in MS15-044, 3072310 in MS15-080, 3048077 in MS15-044, 3080333 in MS15-080 Restart Required: Requires Restart 14 MS15-128: Security Update for Microsoft Graphics Component to Address Remote Code Execution (3104503)
- 15. Shavlik Confidential Maximum Severity: Critical Affected Products: Silverlight Description: This security update resolves vulnerabilities in Microsoft Silverlight. The most severe of the vulnerabilities could allow remote code execution if Microsoft Silverlight incorrectly handles certain open and close requests that could result in read- and write-access violations. To exploit the vulnerability, an attacker could host a website that contains a specially crafted Silverlight application and then convince a user to visit a compromised website. The attacker could also take advantage of websites containing specially crafted content, including those that accept or host user-provided content or advertisements. Impact: Remote Code Execution Fixes 3 vulnerabilities: CVE-2015-6114, CVE-2015-6165, CVE-2015-6166, Replaces: 3080333 in MS15-080, Restart Required: Does not require restart 15 MS15-129: Security Update for Silverlight to Address Remote Code Execution (3106614)
- 16. Shavlik Confidential Maximum Severity: Critical Affected Products: Windows Description: This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains specially crafted fonts. Impact: Remote Code Execution Fixes 1 vulnerabilities: CVE-2015-6130 Replaces: 2957509 in MS14-036 Restart Required: Requires Restart 16 MS15-130: Security Update for Microsoft Uniscribe to Address Remote Code Execution (3108670)
- 17. Shavlik Confidential Maximum Severity: Critical Affected Products: Office Description: This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights. Impact: Remote Code Execution Fixes 6 vulnerabilities: CVE-2015-6040, CVE-2015-6118, CVE-2015-6122, CVE-2015-6124 (Exploited in Wild), CVE-2015-6172, CVE-2015-6177 Replaces: 2837610 in MS15-081, 2598244 in MS15-081, 3101513 in MS15-116, 3101560 in MS15-116 Restart Required: May Require Restart 17 MS15-131: Security Update for Microsoft Office to Address Remote Code Execution (3116111)
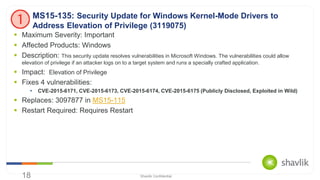
- 18. Shavlik Confidential Maximum Severity: Important Affected Products: Windows Description: This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to a target system and runs a specially crafted application. Impact: Elevation of Privilege Fixes 4 vulnerabilities: CVE-2015-6171, CVE-2015-6173, CVE-2015-6174, CVE-2015-6175 (Publicly Disclosed, Exploited in Wild) Replaces: 3097877 in MS15-115 Restart Required: Requires Restart 18 MS15-135: Security Update for Windows Kernel-Mode Drivers to Address Elevation of Privilege (3119075)
- 19. Shavlik Confidential Maximum Severity: Priority 1 Affected Products: Flash Player, AIR Description: Adobe has released security updates for Adobe Flash Player. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system.. Impact: Security Feature Bypass, Code Execution Fixes 78 vulnerabilities: See notes for list… Replaces: All previous versions Restart Required: May Require Restart 19 APSB15-32: Security updates available for Adobe Flash Player
- 20. Shavlik Confidential Maximum Severity: High Affected Products: Google Chrome Description: The stable channel has been updated to 47.0.2526.80 for Windows, Mac, and Linux. This release contains an update to Adobe Flash Player (20.0.0.228) and security fixes.. Impact: type confusion, use-after-free, escaping issues Fixes 7+ vulnerabilities: CVE-2015-6788, CVE-2015-6789, CVE-2015-6790, CVE-2015-6791 Replaces: All previous versions Restart Required: Browser Reboot Required 20 Chrome-154: Google Chrome 47.0.2526.80
- 21. Shavlik Confidential Maximum Severity: Important Affected Products: Microsoft Windows Description: This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow remote code execution if an attacker accesses a local system and runs a specially crafted application. Impact: Remote Code Execution Fixes 3 vulnerabilities: CVE-2015-6128, CVE-2015-6132, CVE-2015-6133 Replaces: 3101246 in MS15-122, Restart Required: May Require Restart 21 MS15-132: Security Update for Microsoft Windows to Address Remote Code Execution (3116162)
- 22. Shavlik Confidential Maximum Severity: Important Affected Products: Microsoft Windows Description: This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to a target system and runs a specially crafted application that, by way of a race condition, results in references to memory locations that have already been freed. Microsoft Message Queuing (MSMQ) must be installed and the Windows Pragmatic General Multicast (PGM) protocol specifically enabled for a system to be vulnerable. MSMQ is not present in default configurations and, if it is installed, the PGM protocol is available but disabled by default. Impact: Elevation of Privilege Fixes 1 vulnerabilities: CVE-2015-6126 Replaces: none Restart Required: Requires Restart 22 MS15-133: Security Update for Windows PGM to Address Elevation of Privilege (3116130)
- 23. Shavlik Confidential Maximum Severity: Important Affected Products: Microsoft Windows Description: This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if Windows Media Center opens a specially crafted Media Center link (.mcl) file that references malicious code. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights. Impact: Remote Code Execution Fixes 1 vulnerabilities: CVE-2015-2478 Replaces: 3087918 in MS15-100, Restart Required: May Require Restart 23 MS15-134: Security Update for Windows Media Center to Address Remote Code Execution (3108669)
- 24. Shavlik Confidential Opera release updates to latest Chrome Frame. 24 Other lower priority updates for December
- 25. Shavlik Confidential25 Review Patch Releases Since November Patch Tuesday • Microsoft: 47 (Non-Security), 0 (Security Advisories), 0 (Security Tool), 6 (Security) • CDBurnerXP: 1 (Non-Security) • Opera: 1 (Security) • RealTimes: 1 (Security) • Skype: 4 (Security) • CoreFTP: 1 (Non-Security) • Cshell: 1 (Non-Security) • Google Drive: 1 (Non-Secuirty) • VMware Player: 1 (Non-Security) • Wireshark: 1 (Security) • GoToMeeting: 1 (Non-Security) • Java 8: 1 (Non-Security) • Adobe Shockwave: 1 (Security) • 7-Zip: 1 (Non-Security) • Gimp: 1 (Non-Security) • WinRAR: 1 (Non-Security) • Adobe Acrobat Reader DC: 1 (Security) • Google Chrome: 1 (Security) • Notepad++: 1 (Security) • Thunderbird: 1 (Security) • Ccleaner: 1 (Non-Security) • Tomcat: 1 (Non-Security) • TeamViewer: 1 (Non-Security) • VDA Core Services: 2 (Non-Security) • Citrix XenApp: 1 (Non-Security) • Dropbox: 1 (Non-Security)
- 26. Q&A
- 27. Shavlik Confidential • Shavlik Protect 9.2 Update 1 is available. Includes 7 fixes for known issues since release on November 19th. • Slide deck and video playback available here: www.shavlik.com/Webinars • Sign up for next months Patch Tuesday Webinar and view webinar playbacks: http://www.shavlik.com/webinars/ • Sign up for Content Announcements: • Email http://www.shavlik.com/support/xmlsubscribe/ • RSS http://protect7.shavlik.com/feed/ • Twitter @ShavlikXML • Follow us on: • Shavlik on LinkedIn • Twitter @ShavlikProtect • Shavlik blog -> www.shavlik.com/blog • Chris Goettl on LinkedIn • Twitter @ChrisGoettl 27 Resources and Webinars
Editor's Notes
- #6: 1 public disclosure 2 exploited in wild
- #10: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Public Disclosure: CVE-2015-6175 Exploited in Wild: CVE-2015-6175
- #11: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Public Disclosure: None
- #12: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Public Disclosure: None You will not see MS15-125 as an individual update. It is included in the CSWU-016 Cumulative Update for Windows 10.
- #13: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Public Disclosure: none A remote code execution vulnerability exists in the way that the VBScript engine renders, when handling objects in memory in Internet Explorer. In a web-based attack scenario, an attacker could host a specially crafted website that is designed to exploit the vulnerability through Internet Explorer and then convince a user to view the website. An attacker could also embed an ActiveX control marked "safe for initialization" in an application or Microsoft Office document that hosts the IE rendering engine. The attacker could also take advantage of compromised websites, and websites that accept or host user-provided content or advertisements. These websites could contain specially crafted content that could exploit the vulnerability. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. The update addresses the vulnerability by modifying how the VBScript scripting engine handle objects in memory.
- #14: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Public Disclosure: none A remote code execution vulnerability exists in Windows Domain Name System (DNS) servers when they fail to properly parse requests. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account. Windows servers that are configured as DNS servers are at risk from this vulnerability. An attacker could create a specially crafted application to connect to a Windows DNS server and then issue malicious requests to the server. The update addresses the vulnerability by modifying how Windows DNS servers parse requests.
- #15: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Publicly Disclosed: There are multiple update packages available for some of the affected software. Do I need to install all the updates listed in the Affected Software table for the software? Yes. Customers should apply all updates offered for the software installed on their systems. If multiple updates apply, they can be installed in any order. Do I need to install these security updates in a particular sequence? No. Multiple updates for a given system can be applied in any sequence. Multiple remote code execution vulnerabilities exist when the Windows font library improperly handles specially crafted embedded fonts. An attacker who successfully exploited these vulnerabilities could install programs; view, change, or delete data; or create new accounts with full user rights. There are multiple ways an attacker could exploit the vulnerabilities, such as by convincing a user to open a specially crafted document, or by convincing a user to visit an untrusted webpage that contains embedded fonts. The security update addresses the vulnerabilities by correcting how the Windows font library handles embedded fonts.
- #16: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Publicly Disclosed: Why is the update listed in this bulletin also denoted in other bulletins releasing this month? Since bulletins are broken out by the security vulnerabilities they address, not by the update packages being released, it is possible for separate bulletins to reference the same update if the fixes for their respective vulnerabilities have been consolidated into a single update package. In such situations it is also possible for the vulnerabilities described in the one bulletin to have completely different severity and impact ratings than the vulnerabilities described in the other bulletin. This is frequently the case with cumulative updates for products such as Internet Explorer or Silverlight where singular updates contain fixes very different security vulnerabilities being discussed in separate bulletins. Note that identical update files shipping with multiple bulletins do not need to be installed more than once. To exploit the vulnerability, an attacker could host a website that contains a specially crafted Silverlight application and then convince a user to visit the compromised website. The attacker could also take advantage of websites containing specially crafted content, including those that accept or host user-provided content or advertisements. For example, an attacker could display specially crafted web content by using banner advertisements or by using other methods to deliver web content to affected systems. In all cases, however, an attacker would have no way to force users to visit a compromised website. Instead, an attacker would have to convince a user to visit the website, typically by enticing the user to click a link in an email or in an Instant Messenger message. In the web-browsing scenario, an attacker who successfully exploited this vulnerability could obtain the same permissions as the currently logged-on user. If a user is logged on with administrative user rights, an attacker could take complete control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. The update addresses the vulnerability by correcting how Microsoft Silverlight handles certain open and close web requests.
- #17: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Publicly Disclosed: A remote code execution vulnerability exists when Windows Uniscribe improperly parses specially crafted fonts. An attacker who successfully exploited the vulnerability could install programs; view, change, or delete data; or create new accounts with full user rights. There are multiple ways an attacker could exploit the vulnerability, such as by convincing a user to open a specially crafted document, or by convincing a user to visit an untrusted webpage that contains embedded fonts. The security update addresses the vulnerability by correcting how Windows parses fonts.
- #18: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Exploited in Wild: CVE-2015-6124 I have Microsoft Word 2010 installed. Why am I not being offered the 3114403 update? The 3114403 update only applies to systems running specific configurations of Microsoft Office 2010. Some configurations will not be offered the update. Multiple remote code execution vulnerabilities exist in Microsoft Office software when the Office software fails to properly handle objects in memory. An attacker who successfully exploited these vulnerabilities could run arbitrary code in the context of the current user. If the current user is logged on with administrative user rights, an attacker could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. Exploitation of these vulnerabilities requires that a user open a specially crafted file with an affected version of Microsoft Office software. In an email attack scenario an attacker could exploit the vulnerabilities by sending the specially crafted file to the user and convincing the user to open the file. In a web-based attack scenario an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) that contains a specially crafted file that is designed to exploit the vulnerabilities. An attacker would have no way to force users to visit the website. Instead, an attacker would have to convince users to click a link, typically by way of an enticement in an email or Instant Messenger message, and then convince them to open the specially crafted file.
- #19: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Public Disclosure: CVE-2015-6175 Exploited in Wild: CVE-2015-6175 This is a Kernel update. It is recommended to test thoroughly before deploying. Multiple elevation of privilege vulnerabilities exist due to the way the Windows kernel handles objects in memory. An attacker who successfully exploited the vulnerabilities could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. To exploit this vulnerabilities, an attacker would first have to log on to the system. An attacker could then run a specially crafted application that could exploit the vulnerabilities and take control over an affected system. The security update addresses the vulnerabilities by correcting how the Windows kernel handles objects in memory.
- #20: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Flash Player and all related plug ins must be updated to fully resolve these vulnerabilities. IE, Chrome each have an update to apply, and Firefox will auto update the plug-in typically CVE-2015-8045, CVE-2015-8047, CVE-2015-8048, CVE-2015-8049, CVE-2015-8050, CVE-2015-8418, CVE-2015-8454, CVE-2015-8455, CVE-2015-8055, CVE-2015-8056, CVE-2015-8057, CVE-2015-8058, CVE-2015-8059, CVE-2015-8060, CVE-2015-8061, CVE-2015-8062, CVE-2015-8063, CVE-2015-8064, CVE-2015-8065, CVE-2015-8066, CVE-2015-8067, CVE-2015-8068, CVE-2015-8069, CVE-2015-8070, CVE-2015-8071, CVE-2015-8401, CVE-2015-8402, CVE-2015-8403, CVE-2015-8404, CVE-2015-8405, CVE-2015-8406, CVE-2015-8407, CVE-2015-8408, CVE-2015-8409, CVE-2015-8410, CVE-2015-8411, CVE-2015-8412, CVE-2015-8413, CVE-2015-8414, CVE-2015-8415, CVE-2015-8416, CVE-2015-8417, CVE-2015-8419, CVE-2015-8420, CVE-2015-8421, CVE-2015-8422, CVE-2015-8423, CVE-2015-8424, CVE-2015-8425, CVE-2015-8426, CVE-2015-8427, CVE-2015-8428, CVE-2015-8429, CVE-2015-8430, CVE-2015-8431, CVE-2015-8432, CVE-2015-8433, CVE-2015-8434, CVE-2015-8435, CVE-2015-8436, CVE-2015-8437, CVE-2015-8438, CVE-2015-8439, CVE-2015-8440, CVE-2015-8441, CVE-2015-8442, CVE-2015-8443, CVE-2015-8444, CVE-2015-8445, CVE-2015-8446, CVE-2015-8447, CVE-2015-8448, CVE-2015-8449, CVE-2015-8450, CVE-2015-8451, CVE-2015-8452, CVE-2015-8453.
- #21: Shavlik Priority: Shavlik rates this bulletin as a Priority 1. This means you should update as soon as possible on all systems. Includes update for Flash Plug-In resolving 78 vulnerabilities: Flash Player and all related plug ins must be updated to fully resolve these vulnerabilities. IE, Chrome each have an update to apply, and Firefox will auto update the plug-in typically.
- #22: Shavlik Priority: Shavlik rates this bulletin as a Priority 2. This means the update should be implemented in a reasonable timeframe after adequate testing. Multiple remote code execution vulnerabilities exist when Windows improperly validates input before loading libraries. An attacker who successfully exploited the vulnerabilities could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. To exploit the vulnerabilities, an attacker would need access to the local system and the ability to execute a specially crafted application on the system. The security update addresses the vulnerabilities by correcting how Windows validates input before loading libraries.
- #23: Shavlik Priority: Shavlik rates this bulletin as a Priority 2. This means the update should be implemented in a reasonable timeframe after adequate testing. Microsoft Message Queuing (MSMQ) must be installed and PGM specifically enabled for a system to be vulnerable. MSMQ is not present in default configurations and if it is installed the PGM protocol is available but disabled by default. Shavlik uses a defense in depth approach in cases like this. If the patch can be applied we will offer it, even if the system is not configured in a way that it is currently vulnerable. An elevation of privilege vulnerability exists in the Windows Pragmatic General Multicast (PGM) protocol that is caused when an attacker-induced race condition results in references to memory contents that have already been freed. An attacker who successfully exploited this vulnerability could execute code with elevated privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. To exploit this vulnerability, an attacker would first have to log on to the target system. An attacker could then run a specially crafted application that is designed to create the race condition that leads to elevated privileges. The security update addresses the vulnerability by deferring memory cleanup until the contents of memory no longer need to be accessed.
- #24: Shavlik Priority: Shavlik rates this bulletin as a Priority 2. This means the update should be implemented in a reasonable timeframe after adequate testing. A vulnerability exists in Windows Media Center that could allow remote code execution if Windows Media Center opens a specially crafted Media Center link (.mcl) file that references malicious code. An attacker who successfully exploited this vulnerability could take control of an affected system. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. Workstations are primarily at risk of this vulnerability. To exploit the vulnerability, user interaction is required. In a web-browsing scenario, a user would have to navigate to a compromised website that an attacker is using to host a malicious .mcl file. In an email attack scenario, an attacker would have to convince a user who is logged on to a vulnerable workstation to click a specially crafted link in an email. The security update addresses the vulnerability by correcting how Windows Media Center handles certain resources in the .mcl file.
- #25: Shavlik Priority: Shavlik rates this bulletin as a Priority 3. Consider this update for testing and rollout when convenient. Note: Some 3rd party updates may be non-security, but are still classified in Protect as Security. This is due to the fact that the step from current to this version December include security fixes based on the version currently on a machine. It would only be considered non-security if you were up to the latest version before the non-security release was made available.
- #26: Windows 10 Cumulatives: CSWU-012 – Includes additional security updates. CSWU-013 – Non-Security related. CSWU-014 – Non-Security related. CSWU-015 – Non-Security related. Added support for products: Windows 10 Version 1511, Project 2016, Visio 2016 **Added support for MS15-115, MS15-118, MS15-119, MS15-121 for Server 2003