Robust video data hiding using forbidden zone data hiding and selective embedding
- 1. ROBUST VIDEO DATA HIDING USING FORBIDDEN ZONE DATA HIDING AND SELECTIVE EMBEDDING Under the guidance of: Prof. Rekha Patil Team members: Geeta S Savalgi Pooja Lakha Pooja S Patil
- 2. WHAT IS DATA SECURITY? Protecting a database from destructive forces and the unwanted actions of unauthorized users. INTRODUCTION
- 3. DATA SECURITY TECHNOLOGIES DISK ENCRYPTION HARDWARE BASED MECHANISMS BACKUP S DATA MASKING DATA ERASUR
- 4. DATA HIDING It is the process of embedding information into a host medium. FORBIDDEN ZONE It is defined as the host signal range where no alteration is allowed during data hiding process. SELECTIVE EMBEDDING Here host signal samples, which will be used in data hiding, are determined adaptively. The selection is performed at four stages: Frame selection, frequency band determination, block selection and coefficient selection. KEY TERMS USED IN PROJECT
- 5. To achieve efficient data hiding in video sequence. To utilize systematic RA Codes to encode message bits and frame bits. To allow handling de-synchronization between embedder and decoder. To achieve certain level of robustness against frame drop, repeat and insertion attacks. To use 3-D interleaving. ISSUES AND CHALLENGES
- 6. Successfully utilized in video data hiding applications. Tamper detection in digital videos can be performed efficiently. It is used in fragile applications such as authentication. It provides excess control, copy control in DVD’s. Widely suitable for broader range of application. APPLICATIONS
- 7. The necessity for practical higher dimensional data hiding codes. Adjusting trade-off between robustness(channel code) and imperceptibility(source) by practical means. Design of end-to-end real-life visual applications. MOTIVATIONS
- 8. During video data hiding the quality of the image cannot be preserved. They cannot survive any format conversion or transcoding, without any significant loss of perceptual quality. Efficiently hide data in video and to preserve the quality from the external attacks. PROBLEM STATEMENT
- 9. A new block based data hiding method which makes use of erasure correction capability of repeat accumulates codes. Uses superiority of forbidden zone for low embedding distortion levels. Robust to frame manipulation attacks via frame synchronization markers. SCOPE OF WORK
- 10. The goal of the design process is to produce a model of a system which can be used later to build that system and use this model to build the overall system. DESIGN
- 11. Parallel decoders are used to correct de-sync. The video data hiding methods utilize uncompressed video data where insertions and erasures occur at decoder, causing de-sync. Multiple hronization errors. This scheme is successful only when the number of selected host signal samples is much less than the total number of host signal samples. EXISTING SYSTEM
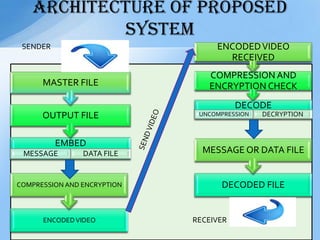
- 12. ARCHITECTURE of proposed system EMBED MESSAGE DATA FILE OUTPUT FILE MASTER FILE ENCODEDVIDEO COMPRESSION AND ENCRYPTION DECODE UNCOMPRESSION DECRYPTION COMPRESSION AND ENCRYPTION CHECK ENCODEDVIDEO RECEIVED DECODED FILE MESSAGE OR DATA FILE SENDER RECEIVER
- 13. ENCODER DECODER
- 14. Substitute bytes Shift rows Add round key Mix columns Substitute bytes Add round key Mix columns Shift keys Add round key Shift keys Substitute bytes Add round key Add round key Inverse mix columns Add round key Inverse sub bytes Inverse shift rows Inverse mix columns Add round key Inverse shift bytes Inverse shift rows Add round key Inverse shift bytes Inverse shift rows EXPAND KEY W(0,3) KEY Round 9 . Round 10 Round 1 Round 9 ound 1
- 15. Implementation is the stage of the project when the theoretical design is turned out into a working system. The implementation stage involves careful planning, investigation of the existing system and it’s constraints. IMPLEMENTATION
- 16. Frame selection is performed and the selected frames are processed block-wise. The selection is performed at four stages: Frame selection Frequency band determination Block selection Coefficient selection ENCRYPTION MODULE
- 17. Let fcur and fpre denote the current and previous frame indices fcur > T, then skip this frame. If fcur = fpre, then skip this frame. Otherwise, process the current frame. fcur< fpre, then the end of the group of frames is reached. DECRYPTION MODULE
- 18. System flow diagram System flow Embed data Spread frames Actual video User give input Msg or data as Data embedded video input Spread a video Encrypted video Decrypt a video View original data or msg Encryption Decryption
- 19. results
- 24. New video data hiding framework that makes use of erasure correction capability of RA codes and superiority of FZDH. It robust to frame manipulation attacks via frame synchronization markers. Typical system parameter are reported for error-free decoding. The results indicate that the framework can be successfully utilized in video data hiding applications. User cannot find the original data. It increases the security. Conclusion
- 25. Incorporation of human visual system based spatio temporal adaption of data hiding method parameters. New multilevel embedding technique . Increase block size to embed more data. Improve commercialization. FUTURE WORK