Session 04 - Arrays in Java
- 1. Java & JEE Training Session 4 – Handling Arrays in Java
- 2. Page 1Classification: Restricted Agenda • Autoboxing and Unboxing in Java • Handling Arrays
- 3. Autoboxing and Unboxing in Java
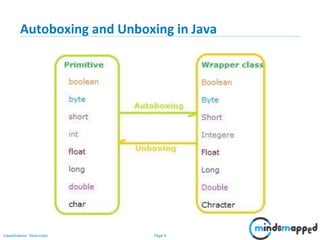
- 4. Page 3Classification: Restricted Autoboxing and Unboxing in Java • Autoboxing is the automatic conversion that the Java compiler makes between the primitive types and their corresponding object wrapper classes. For example, converting an int to an Integer, a double to a Double, and so on. • If the conversion goes the other way, this is called unboxing. • Introduced in JDK 5
- 5. Page 4Classification: Restricted Autoboxing and Unboxing in Java
- 7. Page 6Classification: Restricted Arrays • We need a way to store and manipulate huge quantities of data. • “An array is an indexed sequence of values of the same type.” Examples. • 52 playing cards in a deck. • 5 thousand undergrads at Princeton. • 1 million characters in a book. • 10 million audio samples in an MP3 file. • 4 billion nucleotides in a DNA strand. • 73 billion Google queries per year. • 50 trillion cells in the human body.
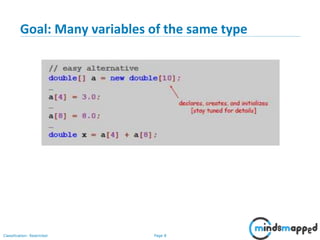
- 8. Page 7Classification: Restricted Goal: Many variables of the same type
- 9. Page 8Classification: Restricted Goal: Many variables of the same type
- 10. Page 9Classification: Restricted Arrays in Java Java has special language support for arrays. • To make an array: declare, create, and initialize it. • To access element i of array named a, use a[i]. • Array indices start at 0. Compact alternative. • Declare, create, and initialize in one statement. • Default initialization: all numbers automatically set to zero.
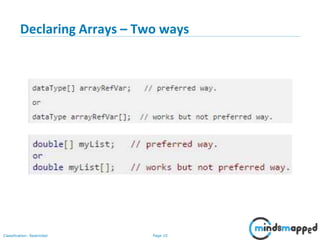
- 11. Page 10Classification: Restricted Declaring Arrays – Two ways
- 12. Page 11Classification: Restricted Exercise: Vector dot product Dot product. Given two vectors x[] and y[] of length N, their dot product is the sum of the products of their corresponding components.
- 13. Page 12Classification: Restricted Array Processing Examples
- 14. Page 13Classification: Restricted Example: Card shuffling algorithm Goal. Given an array, rearrange its elements in random order. • Shuffling algorithm. • In iteration i, pick random card from deck[i] through deck[N-1], with each card equally likely. • Exchange it with deck[i].
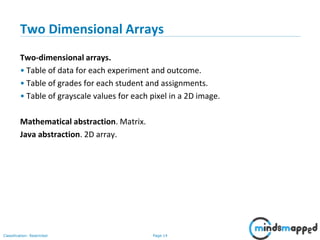
- 15. Page 14Classification: Restricted Two Dimensional Arrays Two-dimensional arrays. • Table of data for each experiment and outcome. • Table of grades for each student and assignments. • Table of grayscale values for each pixel in a 2D image. Mathematical abstraction. Matrix. Java abstraction. 2D array.
- 16. Page 15Classification: Restricted Two Dimensional Arrays in Java • Array access. Use a[i][j] to access element in row i and column j. • Zero-based indexing. Row and column indices start at 0. • a[i] is the i’th row, which is a one dimensional array here.
- 17. Page 16Classification: Restricted Initialize 2D array : Inline initialization
- 18. Page 17Classification: Restricted Example: Matrix Addition
- 19. Page 18Classification: Restricted Example: Matrix Multiplication
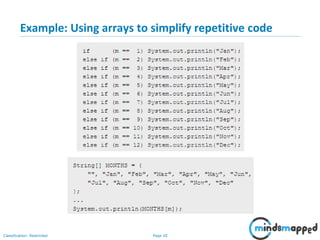
- 20. Page 19Classification: Restricted Example: Using arrays to simplify repetitive code How to simplify writing the above code?
- 21. Page 20Classification: Restricted Example: Using arrays to simplify repetitive code
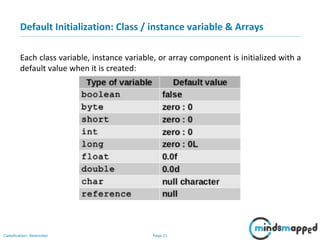
- 22. Page 21Classification: Restricted Default Initialization: Class / instance variable & Arrays Each class variable, instance variable, or array component is initialized with a default value when it is created:
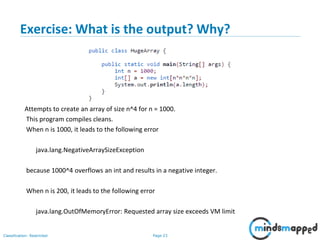
- 23. Page 22Classification: Restricted Exercise: What is the output? Why?
- 24. Page 23Classification: Restricted Exercise: What is the output? Why? Attempts to create an array of size n^4 for n = 1000. This program compiles cleans. When n is 1000, it leads to the following error java.lang.NegativeArraySizeException because 1000^4 overflows an int and results in a negative integer. When n is 200, it leads to the following error java.lang.OutOfMemoryError: Requested array size exceeds VM limit
- 25. Page 24Classification: Restricted Exercise: What is the output? What is wrong with the following code fragment?
- 26. Page 25Classification: Restricted Exercise: What is the output? What is wrong with the following code fragment? It does not allocate memory for a[] with new. The code results in a variable might not have been initialized compile-time error.
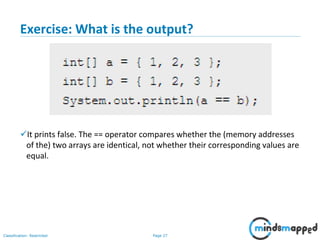
- 27. Page 26Classification: Restricted Exercise: What is the output?
- 28. Page 27Classification: Restricted Exercise: What is the output? It prints false. The == operator compares whether the (memory addresses of the) two arrays are identical, not whether their corresponding values are equal.
- 29. Page 28Classification: Restricted What is the output? • What happens when you try to compile a program with the following statement? int[] a = new int[-17];
- 30. Page 29Classification: Restricted What is the output? • What happens when you try to compile a program with the following statement? int[] a = new int[-17]; It compiles cleanly, but throws a java.lang.NegativeArraySizeException when you execute it.
- 31. Page 30Classification: Restricted What is the output? • Suppose that b[] is an array of 100 elements, with all entries initialized to 0, and that a[] is an array of N elements, each of which is an integer between 0 and 99. What is the effect of the following loop?
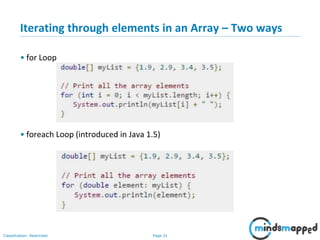
- 32. Page 31Classification: Restricted Iterating through elements in an Array – Two ways • for Loop • foreach Loop (introduced in Java 1.5)
- 33. Page 32Classification: Restricted Arrays – Sorting and Searching • java.util package has API for search and sort • Arrays.sort() – • Default sorting is ascending order • But this can be used with sorting order Collections.reverseOrder() which can be used for sorting in descending order, but can be used only with Object type and not primitive type • Arrays.binarySearch()
- 34. Page 33Classification: Restricted Exercise • Given an array of sorted elements, search for the element requested. • Given a 2D array that is sorted column wise and row wise, write an algorithm to find if an element exists in the matrix or not. Keep the temporal complexity of the algorithm in mind.
- 35. Page 34Classification: Restricted Topics to be covered in next session • Memory Allocation & Garbage Collection • Strings in Java







![Page 9Classification: Restricted
Arrays in Java
Java has special language support for arrays.
• To make an array: declare, create, and initialize it.
• To access element i of array named a, use a[i].
• Array indices start at 0.
Compact alternative.
• Declare, create, and initialize in one statement.
• Default initialization: all numbers automatically set to zero.](https://image.slidesharecdn.com/session04-arraysinjava-slides-180607171250/85/Session-04-Arrays-in-Java-10-320.jpg)
![Page 11Classification: Restricted
Exercise: Vector dot product
Dot product. Given two vectors x[] and y[] of length N, their dot product is
the sum of the products of their corresponding components.](https://image.slidesharecdn.com/session04-arraysinjava-slides-180607171250/85/Session-04-Arrays-in-Java-12-320.jpg)

![Page 13Classification: Restricted
Example: Card shuffling algorithm
Goal. Given an array, rearrange its elements in random order.
• Shuffling algorithm.
• In iteration i, pick random card from deck[i] through deck[N-1], with each
card equally likely.
• Exchange it with deck[i].](https://image.slidesharecdn.com/session04-arraysinjava-slides-180607171250/85/Session-04-Arrays-in-Java-14-320.jpg)
![Page 15Classification: Restricted
Two Dimensional Arrays in Java
• Array access. Use a[i][j] to access element in row i and column j.
• Zero-based indexing. Row and column indices start at 0.
• a[i] is the i’th row, which is a one dimensional array here.](https://image.slidesharecdn.com/session04-arraysinjava-slides-180607171250/85/Session-04-Arrays-in-Java-16-320.jpg)






![Page 25Classification: Restricted
Exercise: What is the output?
What is wrong with the following code fragment?
It does not allocate memory for a[] with new. The code results in a variable
might not have been initialized compile-time error.](https://image.slidesharecdn.com/session04-arraysinjava-slides-180607171250/85/Session-04-Arrays-in-Java-26-320.jpg)

![Page 28Classification: Restricted
What is the output?
• What happens when you try to compile a program with the following
statement?
int[] a = new int[-17];](https://image.slidesharecdn.com/session04-arraysinjava-slides-180607171250/85/Session-04-Arrays-in-Java-29-320.jpg)
![Page 29Classification: Restricted
What is the output?
• What happens when you try to compile a program with the following
statement?
int[] a = new int[-17];
It compiles cleanly, but throws a java.lang.NegativeArraySizeException
when you execute it.](https://image.slidesharecdn.com/session04-arraysinjava-slides-180607171250/85/Session-04-Arrays-in-Java-30-320.jpg)
![Page 30Classification: Restricted
What is the output?
• Suppose that b[] is an array of 100 elements, with all entries initialized to 0,
and that a[] is an array of N elements, each of which is an integer between
0 and 99. What is the effect of the following loop?](https://image.slidesharecdn.com/session04-arraysinjava-slides-180607171250/85/Session-04-Arrays-in-Java-31-320.jpg)