SplunkLive! Paris 2018: Use Splunk for Incident Response, Orchestration and Automation
- 1. Use Splunk for Incident Response, Orchestration and Automation 27 Mars | Paris Younes Khaldi | Sales Engineer
- 2. ▶ Challenges with Security Operations Today ▶ Overview of Splunk Adaptive Response Initiative ▶ Technology behind the Adaptive Response Framework ▶ Demonstrations ▶ How to build your own AR Action ▶ Resources Agenda
- 3. Incident Response Slow Alert Noise Tools Problem Many tools Disparate tools Skills Lack of skills Retention Training Scale Horizontal and Vertical Orchestration Automation Security Operations Need to Change
- 4. Orchestration ▶ Brings together or integrates different technologies and tools ▶ Provides the ability to coordinate informed decision making, formalize and automate responsive actions ▶ Security-specific or non-security- specific Automation ▶ Focus is on how to make machines do task-oriented "human work” ▶ Improve repetitive work, with high confidence in the outcome ▶ Allows multiple tasks or "playbooks" to potentially execute numerous tasks ▶ Automation is a subset of orchestration Orchestration vs Automation
- 6. Incident Response Takes Significant Time 7 Source: SANS 2017 Incident Response Survey
- 7. Where Does Your Time Go? When working an incident, which phase generally takes the longest to complete in your organization? Day in the life of a security professional survey © 2016 EMA, Inc. Too much time lost: time-to-decide time-to-act = increased risk/impact
- 8. Time-to-Contain + Time-to-Respond = 72% When working an incident, which phase generally takes the longest to complete in your organization? Day in the life of a security professional survey © 2016 EMA, Inc.
- 10. Search and Investigate Analytics-Driven Security Index Untapped Data: Any Source, Type, Volume On- Premises Private Cloud Public Cloud Storage Online Shopping Cart Telecoms Desktops Security Web Services Networks Containers Web Clickstreams RFID Smartphones and Devices Servers Messaging GPS Location Packaged Applications Custom Applications Online Services DatabasesCall Detail Records Energy Meters Firewall Intrusion Prevention Splunk Enterprise Security 600+ Security Apps Splunk User Behavior Analytics Monitoring, Correlations, Alerts Dashboards and Reports Analytics and Virtualization Adaptive Response Employee Info Asset and CMDB Threat Intelligence Applications Data Stores External Lookups Platform for Operational Intelligence
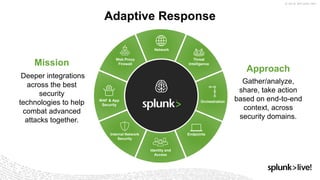
- 11. Adaptive Response Identity and Access Internal Network Security Endpoints OrchestrationWAF & App Security Threat Intelligence Network Web Proxy FirewallMission Deeper integrations across the best security technologies to help combat advanced attacks together. Approach Gather/analyze, share, take action based on end-to-end context, across security domains.
- 12. ▶ File analysis (Sandbox/malware analysis) ▶ IP reputation ▶ Hunt File: look for a particular file/process on endpoints (Forensics) ▶ Run query into Splunk (check who received/clicked on the email) ▶ Quarantine Device: disconnect a device from the network via NAC ▶ Sending Service Ticket to Reimage Workstation! ▶ Later: Malware reverse engineering Journey of an incident response: Phishing investigation and remediation
- 13. Cloud Security Endpoints Orchestration WAF & App Security Threat Intelligence Network Web Proxy Firewall Identity and Access
- 14. “ Security teams must be quicker than ever in processing a vast number of alerts with accuracy, and we could no longer afford the manual method of coordinating across various siloes of security for incidence response within our environments.” Tobias Langbein, security architect Swisscom “ Leveraging the ForeScout Extended Module for Splunk via Adaptive Response, we can increase our holistic data defense and security to minimize the impact of malware and data breaches. …This will enable us to minimize the time and resources needed to respond to emerging threats.” Clayton Colwell, associate security engineer, Brown-Forman Corporation. “ …The Adaptive Response capabilities in Splunk Enterprise Security provide the centerpiece of a flexible, ecosystem- driven approach to combat advanced attacks through a more coordinated, automated response.” Scott Crawford research director of information security 451 Research What the community is saying
- 16. How To Interact With AR Suggest Next StepsAutomatically With Notables Run Ad-Hoc
- 17. Adaptive Response Actions (Examples) AUTOMATIO N Automatically With Notables
- 18. Adaptive Response Actions (Examples) AUTOMATIO NCategory – Information gathering, Information conveyance, Permissions control Task – Create, Update, Delete, Allow, Block Subject – What will be acted upon (network, endpoint, etc.) Vendor – Providing the action. Ex.: Splunk, Ziften, Palo Alto Networks, etc.
- 19. Adaptive Response Actions (Examples) AUTOMATIO N
- 20. Accelerate Detection, Investigation & Response ▶ Use the correlation search builder to configure, automate and attach the results to notable events ▶ In incident review, configure and execute ad-hoc responses and queries across the security ecosystem ▶ Use the actions dashboard to search and review responses taken and their results
- 22. AWS Adaptive Response AR actions using AWS Lambda
- 23. ▶ Detect suspicious activity ▶ Tag machine ▶ Change security group to lockdown ▶ Take snapshot of infected instance ▶ Send email to instance owner (Terminate) What we will show
- 25. Anomali Threatstream Splunk App Adaptive Response Capabilities Information gathering AR actions using Anomali
- 26. Splunk’s powerful analytics with Anomali’s threats ▶ Anomali is a powerful Threat Hunting engine that compares millions of Indicator Of Compromise (IOC) against internal traffic ▶ Match threats from Anomali provides security teams the tools to research and investigate IOCs ▶ Anomali delivers critical insight into IOC threats ▶ Splunk’s users can access this information, or pivot to the Anomali portal
- 27. ▶ Detect suspicious communications ▶ Dispatch “notable event” data to Anomali for further analysis. ▶ Compare against ThreatStream’s database of threat intelligence ▶ Write information back to the Splunk’s investigation timeline What we will show
- 29. The Development Building your own AR Actions
- 30. ▶ Option 1: Develop from scratch ▶ Option 2: Use the Splunk Add-on Builder (Recommended) ▶ Option 3: Outsource to a development partner Development Options
- 31. Option #1 Dev From Scratch ▶ Start here: • Guide to developing AR actions for ES • Code example of AR action ▶ Pretty easy, but there is a better way…
- 32. Option #2: Splunk Add-on Builder Validate Add-on • Score health of CIM compliance and naming conventions • Verify readiness for Certification • Detect problems with field extraction Define Knowledge Extraction • Extract and define fields using automated event analysis • Map fields to CIM with click of button Create Modular Input and Custom Alert • Create required directory structure, configuration/XML files, Python scripts • Multiple input types supported, including shell, REST, and Splunk Python SDK • Build and validate Custom Alert Action (optional) Create Add-on using step by step process free download splunkbase.com
- 33. ▶ AR Technical Brief on splunk.com • https://www.splunk.com/pdfs/technical-briefs/using-splunk-adaptive-response.pdf ▶ Adaptive Response framework • http://dev.splunk.com/view/enterprise-security/SP-CAAAFBE ▶ Video Demos • Carbon Black AR • Recorded Future • Anomali Resources
- 34. © 2018 SPLUNK INC. 1. Adaptive Response helps accelerate Incident Detection, Investigation and Response 2. Use Adaptive Response framework for multi-vendor security workflow orchestration and automation 3. Use with IT and Security domains to solve a range of security use cases Mitigate Incident Response Challenges With Orchestration and Automation Key Takeaways
- 35. Attend .conf18 .conf is Splunk’s premier education and thought leadership event for thousands of IT and business professionals who are keen to use machine data insights to find answers. .conf18 | October 1 - 4, 2018 University | September 29 – October 1, 2018 Walt Disney World Swan and Dolphin Resort | Orlando, Florida “.conf is an exciting collection of technical sessions, hands-on demos and social networking with industry professionals and users. I can’t wait for .conf18.” – Michael Deisher, Systems Analyst, Visa Registration opens April 10th!
- 36. © 2018 SPLUNK INC. Thank You! https://www.surveymonkey.com/r/SLParis2018
- 37. Q&A