Underwater wirelesscommunication
- 1. SECURING UNDERWATER WIRELESS COMMUNICATION NETWORKS Presented By Ku. Devyani B. vaidya
- 2. OUTLINE INTRODUCTION HISTORY NECCESITY OF UWCNs ATTACKS AND COUNTER MEASURES SECURITY REQUIREMENT PROPOSED SECURITY MECHANISM APPLICATIONS OF UWCNs DISADVANTAGES OF UWCNs CONCLUSION REFERENCES
- 3. INTRODUCTION .Underwater wireless communication networks (UWCNs) are constituted by sensors and autonomous underwater vehicles (AUVs) that interact to perform specific applications such as underwater monitoring . Sensors Nodes are simply nodes energy constrained devices that have ability of sensing the surrounding environment. Sink also known as base station, is a more powerful node that behaves as an interface between the sensor nodes and the clients. Autonomous Underwater Vehicles (AUVS) that interact to perform specific applications such as underwater monitoring.
- 4. HISTORY The science of underwater communication began in 1490 when Leonardo da Vinci stated. In 1687 , Issac Newton wrote his Mathematical Principles of Natural Philosophy which included the first mathematical treatment of sound of water.
- 5. NECESSITY OF UWCNs Wired underwater is not feasible in all situations as shown below- Temporary experiments Breaking of wires Significant cost of deployment Experiment over long distances Radio waves do not propagate well underwater due to high energy absorption of water. Therefore UWCNs are based on acoustic links characterized by large propagation delay. It cannot rely on GPS.
- 6. ATTACKS AND COUNTERMEASURES Underwater wireless communication networks are particularly vulnerable to malicious attacks due to the high bit error rates, large and variable propagation delays and low bandwidth of acoustic channels. Several methods are proposed to secure UWCN . Three schemes are there namely secure time synchronaization, localization and routing in UWCN.
- 7. Jamming Wormh ole attacks Sybil attack Selective Forwardi ng Acknowl edgment Spoofing ATTACKS Hello Flood attack Sinkhole Attacks ATTACKS AND COUNTER MEASURES
- 8. JAMMING Method of Attack A jamming attack consists of interfering with the physical channel by putting up carriers on the frequencies neighbor nodes use to communicate . Countermeasures Spread spectrum techniques Sensors can switch to sleep mode
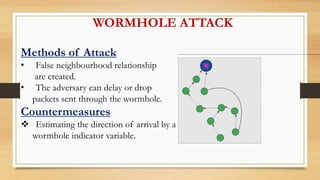
- 9. WORMHOLE ATTACK Methods of Attack • False neighbourhood relationship are created. • The adversary can delay or drop packets sent through the wormhole. Countermeasures Estimating the direction of arrival by a wormhole indicator variable.
- 10. SINKHOLE ATTACK Methods of Attack • A malicious node attempts to attract traffic from a particular area towards it by announcing that it is a high quality route. Countermeasures Geographical routing. Authentication of nodes exchanging routing information.
- 11. HELLO FLOOD ATTACK Methods of Attack • A node receiving a hello packet from a malicious node may interpret that the adversary is a neighbor node. Countermeasures Bidirectional link verification. Authentication is a possible defense.
- 12. SELECTIVE FORWARDING Methods of Attack • Malicious nodes drop certain messages instead of forwarding them to hinder routing. Countermeasures Multipath routing. Authentication.
- 13. Sybil Attack Methods of Attack • Sybil attack is defined as a malicious node illegitimately taking on multiple identities. • Attacker with multiple identities pretend to be in many places at once. Countermeasures Authentication. Position verification.
- 14. Acknowledgement Spoofing Methods of Attack • A malicious node overhearing packets sent to neighbor nodes use the information to spoof acknowledgements. Countermeasures Encryption of all packets sent through the networks.
- 15. SECURITY REQUIREMENT Authentication :-Proof that data was sent by a legitimate user. Confidentiality:- Information is not accessible to unauthorized parties. Integrity:-Information is not altered. Availability:-Data should be available when needed by an authorized user.
- 16. PROPOSED SECURITY MECHANISM Securing underwater wireless communication : Secure time synchronization. Secure localization. Secure routing.
- 17. SECURE TIME SYNCHRONIZATION: Why is Time Synchronization important ? Location and proximity siblings Maintain ordering of messages Internetwork coordination Energy efficiency
- 18. SECURE LOCALIZATION: Why is Localization important ? Sensor tasks . Making routing decisions . The attacker makes the node think it is somewhere different from actual location.As a result wrong decisions happen. Secure localization gives the guarantee of correctness despite of presence of intruders.It is the process for each sensor node to locate its position in the network.
- 19. SECURE ROUTING: Why is routing important ? A sensor routing rejects the routing paths containing malicious nodes. It is specially challenging in UWCNs due to the large propagation delays,low bandwidth,difficulty of battery refills of underwater sensors and dynamic topologies.
- 21. Search and rescue missions under water.
- 22. Environmental monitoring to gather oceanographic data.
- 24. DISADVANTAGES of UWCNs Battery power is limited and can not be recharged easily. The available bandwidth is severely limited. Long and variable propagation delays. Multipath and fading problems. High bity error rate.
- 25. CONCLUSION Wireless technology will play a vital role in many application areas that are not possible in past. The main challenges related to secure time synchronization,localization and routing have been surveyed. Since the deployment of the proposed system is still in its development stage , an account of actual implementation has not been provided in this paper. The research issues of UWCNs remain wide open for future investigation.
- 26. REFERENCES M.C Domingo ,”Securing underwater wireless communication networks”, Journal ,IEEE Wireless Communications archive. Volume 18 Issue 1, February 2011 I.F. Akyildiz, D. Pompili, and T. Melodia, “Underwater Acoustic Sensor Networks: Research Challenges,” Ad Hoc Net., vol. 3, no. 3, Mar. 2005. W. Wang et al., “Visualization of Wormholes in Under-water Sensor Networks: A Distributed Approach,” Int’l. J. Security Net., vol. 3, no. 1, 2008. F. Hu, S. Wilson, and Y. Xiao, “Correlation-Based Security in Time Synchronization of Sensor Networks,” Proc. IEEE WCNC, 2008. C. Tian et al., “Tri-Message: A Lightweight Time Synchronization Protocol for High Latency and Resource-Constrained Networks,” Proc. IEEE ICC, 2009. C. Tian et al., “Localization and Synchronization for 3D Underwater Acoustic Sensor Networks,” in Ubiquitous Intelligence and Computing, LNCS, Springer, 2007, pp. 622–31.