Writing exploits
- 1. Writing Exploits Nethemba s.r.o. norbert.szetei@nethemba.com www.nethemba.com www.nethemba.com
- 2. Motivation Basic code injection W^X (DEP), ASLR, Canary (Armoring) Return Oriented Programming (ROP) Tools of the Trade Metasploit www.nethemba.com
- 3. A Brief History 08/11/1996 Phrack #49 Smashing The Stack For Fun And Profit, Elias Levy “ … Code that does this is said to smash the stack, and can cause return from the routine to jump to a random address. This can produce some of the most insidious datadependent bugs known to mankind.” www.nethemba.com
- 4. Stack Frame Low Memory Address void func(int a, int b, int c) { char buffer1[BUFSIZE]; char buffer2[BUFSIZE]; buffer2 } int main(int argc, char **argv) { buffer1 func(10, 20, 30); EBP } EIP prologue, epilogue 10 push ebp mov esp, ebp 20 mov ebp, esp pop ebp 30 sub esp, $const ret High Memory Address www.nethemba.com
- 5. Buffer Overflow Low Memory Address void func(char *src) { char dest[64]; strcpy(dest, src); } int main(int argc, char **argv) { dest func(argv[1]); EBP } EIP args High Memory Address www.nethemba.com
- 6. Buffer Overflow Low Memory Address void func(char *src) { char dest[64]; strcpy(dest, src); } int main(int argc, char **argv) { SHELLCODE func(argv[1]); JUNK } JMP TO SC JUNK High Memory Address www.nethemba.com
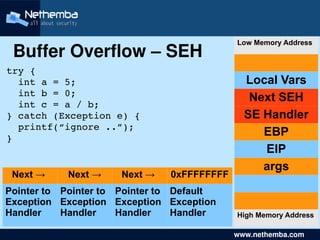
- 7. Low Memory Address Buffer Overflow – SEH try { int a = 5; Local Vars int b = 0; Next SEH int c = a / b; } catch (Exception e) { SE Handler printf(“ignore ..”); } EBP EIP args Next → Next → Next → 0xFFFFFFFF Pointer to Pointer to Pointer to Default Exception Exception Exception Exception Handler Handler Handler Handler High Memory Address www.nethemba.com
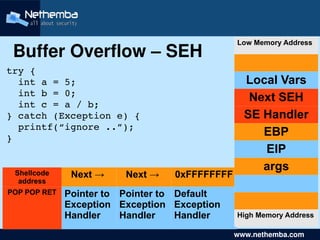
- 8. Low Memory Address Buffer Overflow – SEH try { int a = 5; Local Vars int b = 0; Next SEH int c = a / b; } catch (Exception e) { SE Handler printf(“ignore ..”); } EBP EIP args Shellcode Next → Next → 0xFFFFFFFF address POP POP RET Pointer to Pointer to Default Exception Exception Exception Handler Handler Handler High Memory Address www.nethemba.com
- 9. Low Memory Address Stack cookies – canaries Local Vars Protection provided by the compiler Canary (/gs, fstackprotector, StackGuard, Next SEH ProPolice) SE Handler Can rearrange the stack layout, so EBP string variables are on higher EIP addresses and cannot overwrite args other local variables Contain “bad” characters (0x00, 0xFF) High Memory Address www.nethemba.com
- 10. Stack cookies – canaries Usually a challenge Entropy weaknesses (24bit entropy on Ubuntu, can by bypassed in reasonable time) Sometimes helps to overwrite SEH Cannot protect from buffer overflows in heap www.nethemba.com
- 11. Protection DEP Stack is no longer executable W^X Both HW (NX bit) and software support Prevent basic buffer overflows Four policy levels on Windows platform: Optin, OptOut, AlwaysOn, AlwaysOff Can be bypassed by “returntolibc” www.nethemba.com
- 12. Return to LIBC The most generic method to bypass NX No executable code in stack EIP is overwritten by library function (system()) Parameters are passed via stack Chained “return to libc” No loops, conditional jumps, complicated things 28/12/2001 Phrack #58, Advanced returninto lib(c) exploits www.nethemba.com
- 13. Low Memory Address Return to LIBC Low Memory Address uuu ←basic buffer overflow Local Vars Local Vars EBP EBP EIP system() args return to libc → EIP JUNK “/bin/sh0” High Memory Address High Memory Address www.nethemba.com
- 14. ASLR Address Stack Layout Randomization Including Libraries, Heap, Stack But not necessary in all libraries You need at least one module without ASLR for bypassing in Windows Implementation weaknesses Can by bypassed by format string exploits www.nethemba.com
- 15. Format String Attacks int main(int argc, char **argv) { printf(“%s”, argv[1]); // correct printf(argv[1]); // wrong } ● Reading, writing from arbitrary memory ● Direct parameter access via %<num>$ ● Writing via %n, %hn (2 bytes) ● 28/07/2002 Phrack #59, Advances in format string exploitation www.nethemba.com
- 16. Return Oriented Programming ● The successor of “return to libc” technique ● Small number of instructions ending with “ret” (Gadgets) chained together ● If we find them enough, we have the Turing Machine ● Fixed Memory location for data interchange, usually in .data section ● 2 registers are usually efficient www.nethemba.com
- 17. Return Oriented Programming ● You can bypass character restrictions (neg) ● No injected code, just rewritten stack ● ESP determines which instructions you execute ● Automated by tools (ropeme, ROPGadget) # execve /bin/sh bindport 8080 generated by RopGadget v3.3 p += pack("<I", 0x08050dda) # pop %edx | ret p += pack("<I", 0x080cd6a0) # @ .data p += pack("<I", 0x080a49f6) # pop %eax | ret p += "//us" p += pack("<I", 0x080796ed) # mov %eax,(%edx) | ret ... www.nethemba.com
- 18. Return Oriented Programming ● We can build the custom stack at fixed location (bypass ASLR) ● .data, .bss (readelf) ● Multistage exploit ● GOT entry overwriting offset = execve() printf() execve() = printf() + offsef ● Countermeasure: Position Independent Executable (PIE) www.nethemba.com
- 19. Metasploit ● msfpescan, msfelfscan, msfmachscan ● irb, framework for exploits development ● tools/ (memdump, metasm_shell, pattern_create.rb, pattern_offset.rb, nasm_shell) ● mixins www.nethemba.com
- 20. Immunity Debugger ● 'mona' (successor of pvefindaddr) ● skeleton for metasploit exploit can by generated with Immunity Debugger (mona plugin) www.nethemba.com
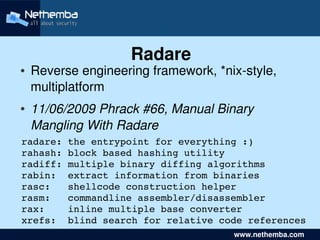
- 21. Radare ● Reverse engineering framework, *nixstyle, multiplatform ● 11/06/2009 Phrack #66, Manual Binary Mangling With Radare radare: the entrypoint for everything :) rahash: block based hashing utility radiff: multiple binary diffing algorithms rabin: extract information from binaries rasc: shellcode construction helper rasm: commandline assembler/disassembler rax: inline multiple base converter xrefs: blind search for relative code references www.nethemba.com
- 22. Wargames ● http://overthewire.org ● http://smashthestack.org www.nethemba.com
- 23. References ● http://www.radare.org/get/radare.pdf ● https://www.metasploit.com www.nethemba.com
- 24. Any questions? Thank you for listening Norbert Szetei, CEH www.nethemba.com




![Stack Frame
Low Memory Address
void func(int a, int b, int c) {
char buffer1[BUFSIZE];
char buffer2[BUFSIZE];
buffer2
}
int main(int argc, char **argv) {
buffer1
func(10, 20, 30); EBP
}
EIP
prologue, epilogue 10
push ebp mov esp, ebp 20
mov ebp, esp pop ebp 30
sub esp, $const ret
High Memory Address
www.nethemba.com](https://image.slidesharecdn.com/writingexploits-120306032813-phpapp01/85/Writing-exploits-4-320.jpg)
![Buffer Overflow
Low Memory Address
void func(char *src) {
char dest[64];
strcpy(dest, src);
}
int main(int argc, char **argv) {
dest
func(argv[1]); EBP
}
EIP
args
High Memory Address
www.nethemba.com](https://image.slidesharecdn.com/writingexploits-120306032813-phpapp01/85/Writing-exploits-5-320.jpg)
![Buffer Overflow
Low Memory Address
void func(char *src) {
char dest[64];
strcpy(dest, src);
}
int main(int argc, char **argv) {
SHELLCODE
func(argv[1]); JUNK
}
JMP TO SC
JUNK
High Memory Address
www.nethemba.com](https://image.slidesharecdn.com/writingexploits-120306032813-phpapp01/85/Writing-exploits-6-320.jpg)






![Format String Attacks
int main(int argc, char **argv) {
printf(“%s”, argv[1]); // correct
printf(argv[1]); // wrong
}
● Reading, writing from arbitrary memory
● Direct parameter access via %<num>$
● Writing via %n, %hn (2 bytes)
● 28/07/2002 Phrack #59, Advances in format string
exploitation
www.nethemba.com](https://image.slidesharecdn.com/writingexploits-120306032813-phpapp01/85/Writing-exploits-15-320.jpg)