Mobility Management in mobile communications.ppt
- 2. Outline • Overview of the PCS system architecture • Mobility management
- 3. PCS system architecture • The mobile service area is covered by a set of base stations (BSs), which are responsible for relaying the calls to and from the mobile stations (MSs) located in their coverage areas (or cells). • The BSs are connected to mobile switching centers (MSCs) by land links. • MSC • a telephone exchange configured specifically for mobile applications. • interfaces the MSs (via BSs) with the PSTN. • Databases are used for roaming management: • Home location register (HLR) • Visitor location register (VLR) • There are two aspects of mobility in a PCS network: • Handoff • Roaming
- 5. Handoff •When a mobile user is engaged in conversation, the MS is connected to a BS via a radio link. •If the mobile user moves to the coverage area of another BS, the radio link to the old BS is eventually disconnected, and a radio link to the new BS should be established to continue the conversation. •This process is variously referred to as automatic link transfer, handover, or handoff.
- 6. Roaming • When a mobile user moves from one PCS system (e.g., the system in New York City) to another (e.g., the system in Los Angeles), the system should be informed of the current location of the user. Otherwise, it would be impossible to deliver the services to the mobile user. • To support mobility management, protocols such as EIA/TIA Interim Standard 41 (IS 41 ‑ or ANSI 41) or ‑ Global System for Mobile Communications (GSM) Mobile Application Part (MAP) have been defined for PCS networks.
- 7. Handoff • Three strategies have been proposed to detect the need for handoff: •mobile controlled handoff (MCHO) ‑ •network controlled handoff (NCHO) ‑ •mobile assisted handoff (MAHO) ‑
- 8. Mobile Controlled Handoff (MCHO) ‑ • The MS continuously monitors the signals of the surrounding BSs and initiates the handoff process when some handoff criteria are met. • MCHO is used in DECT and PACS.
- 9. Network Controlled Handoff (NCHO) ‑ • The surrounding BSs measure the signal from the MS, and the network initiates the handoff process when some handoff criteria are met. • NCHO is used in CT 2 Plus ‑ and AMPS.
- 10. Mobile Assisted Handoff (MAHO) ‑ • The network asks the MS to measure the signal from the surrounding BSs. The network makes the handoff decision based on reports from the MS. • MAHO is used in GSM and IS 95 CDMA ‑ .
- 11. Two types of handoff • The BSs involved in the handoff may be connected to the same MSC (inter cell handoff ‑ or inter BS handoff ‑ ) • The BSs involved in the handoff may be connected to two different MSCs (inter system handoff or inter MSC handoff ‑ ).
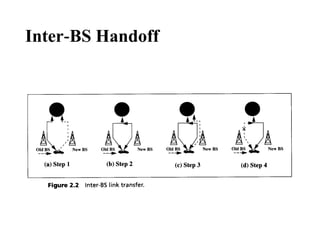
- 12. Inter BS Handoff ‑ •The new and the old BSs are connected to the same MSC. •Assume that the need for handoff is detected by the MS; the following actions are taken: • 1. The MS momentarily suspends conversation and initiates the handoff procedure by signaling on an idle (currently free) channel in the new BS. Then it resumes the conversation on the old BS. • 2. Upon receipt of the signal, the MSC transfers the encryption information to the selected idle channel of the new BS and sets up the new conversation path to the MS through that channel. The switch bridges the new path with the old path and informs the MS to transfer from the old channel to the new channel.
- 13. Inter BS Handoff ‑ •3. After the MS has been transferred to the new BS, it signals the network, and resumes conversation using the new channel. •4. Upon receipt of the handoff completion signal, the network removes the bridge from the path and releases resources associated with the old channel. •This handoff procedure is used with the mobile controlled handoff strategy ‑
- 15. Inter BS Handoff ‑ • For the network controlled handoff strategy ‑ , all handoff signaling messages are exchanged between the MS and the old BS though the failing link. • The whole process must be completed as quickly as possible, to ensure that the new link is established before the old link fails.
- 16. Inter BS Handoff ‑ • If the new BS does not have an idle channel, the handoff call may be dropped (or forced to terminate). • The forced termination probability is an important criterion in the performance evaluation of a PCS network. • Forced termination of an ongoing call is considered less desirable than blocking a new call attempt. • Most PCS networks handle a handoff in the same manner as a new call attempt. That is, if no channel is available, the handoff is blocked and the call is held on the current channel in the old cell until the call is completed or when the failing link is no longer available. • This is referred to as the non-prioritized scheme.
- 17. Channel Assignment Schemes • To reduce forced termination and to promote call completion, three channel assignment schemes have been proposed: • Reserved channel scheme • Queuing priority scheme • Subrating scheme
- 18. Reserved channel scheme • Similar to the non-prioritized scheme, except that some channels in each BS are reserved for handoff calls.
- 19. Queuing priority scheme • Adjacent coverage areas of BSs may overlapped. • Thus, there is a considerable area where a call can be handled by either BS. This area is called the handoff area. • If no channel is available in the new BS during handoff, the new BS buffers the handoff request in a waiting queue. • The MS continues to use the channel with the old BS until either a channel in the new BS becomes available (and the handoff call is connected) or the MS moves out of the handoff area (and the call is forced to terminate).
- 20. Subrating scheme •Creates a new channel for a handoff call by sharing resources with an existing call if no channel is available in the new BS. •Subrating means an occupied full rate channel is ‑ temporarily divided into two channels at half the original rate: • one to serve the existing call • and the other to serve the handoff request. •When occupied channels are released, the subrated channels are immediately switched back to full rate ‑ channels.
- 21. Inter BS Handoff ‑ • These handoff schemes can significantly reduce the probability of forced termination as well as the probability of call incompletion (new call blocking plus handoff call forced termination).
- 22. Intersystem Handoff • In intersystem handoff, the new and old BSs are connected to two different MSCs. • We trace the intersystem handoff procedure of IS 41 ‑ , where network controlled handoff ( ‑ NCHO) is assumed. • In this figure, a communicating mobile user moves out of the BS served by MSC A and enters the area covered by MSC B.
- 23. MSC MSC MSC MSC
- 24. Intersystem Handoff • Intersystem handoff requires the following steps: • Step 1. MSC A requests MSC B to perform handoff measurements on the call in progress. MSC B then selects a candidate BS2, BS2, and interrogates it for signal quality parameters on the call in progress. MSC B returns the signal quality parameter values, along with other relevant information, to MSC A.
- 25. Intersystem Handoff • Step 2. MSC A checks if the MS has made too many handoffs recently (this is to avoid, for example, numerous handoffs between BS1 and BS2 a where the MS is moving within the overlapped area) or if intersystem trunks are not available. If so, MSC A exits the procedure. Otherwise, MSC A asks MSC B to set up a voice channel. Assuming that a voice channel is available in BS2, MSC B instructs MSC A to start the radio link transfer.
- 26. Intersystem Handoff • Step 3. MSC A sends the MS a handoff order. The MS synchronizes to BS2. After the MS is connected to BS2, MSC B informs MSC A that the handoff is successful. MSC A then connects the call path (trunk) to MSC B and completes the handoff procedure.
- 27. Intersystem Handoff •In this intersystem handoff process, MSC A is referred to as the anchor MSC, and is always in the call path before and after the handoff, as illustrated in the four cases in Figure 2.4. •This anchor approach is used in all existing mobile phone networks because the re establishment of a ‑ new call path (without involving MSC A) between MS and the new MSC would require extra trunk release/setup operations in PSTN, which is not available or is not cost effective. ‑
- 28. Intersystem Handoff •If the MS moves back to MSC A again, the connection between MSC A and MSC B is removed (handoff backward). •If the MS moves to the third MSC C, then MSC B will be in the call path (handoff to third). •That is, the link between MSC B and MSC A is disconnected, and MSC C connects to MSC A directly. •This process is called path minimization.
- 30. Roaming Management • Two basic operations in roaming management are • registration (or location update), the process whereby an MS informs the system of its current location, and • location tracking, the process during which the system locates the MS. Location tracking is required when the network attempts to deliver a call to the mobile user.
- 31. Roaming Management • The roaming management strategies proposed in the IS 41 ‑ and GSM MAP standards are two level strategies in that ‑ they use a two tier system of ‑ home and visited databases.
- 32. Home Location Register (HLR) • When a user subscribes to the services of a PCS network, a record is created in the system's database, called the home location register (HLR). • The HLR is a network database that stores and manages all mobile subscriptions of a specific operator. • Specifically, the HLR is the location register to which an MS identity is assigned for record purposes, such as directory number, profile information, current location, and validation period.
- 33. Visitor Location Register (VLR) • When the mobile user visits a PCS network other than the home system, a temporary record for the mobile user is created in the visitor location register (VLR) of the visited system. • The VLR temporarily stores subscription information for the visiting subscribers so that the corresponding MSC can provide service. • In other words, the VLR is the "other" location register used to retrieve information for handling calls to or from a visiting mobile user.
- 35. Registration Procedure • Step 1. Suppose that the home system of a mobile user is in Morristown. When the mobile user moves from one visited system (e.g., New York City) to another (e.g., Los Angeles), it must register in the VLR of the new visited system. • Step 2. The new VLR informs the mobile user's HLR of the person's current location the address of the new VLR. The HLR ‑ sends an acknowledgment, which includes the MS's profile, to the new VLR. • Step 3. The new VLR informs the MS of the successful registration. • Step 4. After step 2, the HLR also sends a deregistration message to cancel the obsolete location record of the MS in the old VLR. The old VLR acknowledges the deregistration.
- 36. Call delivery procedure • To originate a call, the MS first contacts the MSC in the visited PCS network. • The call request is forwarded to the VLR for approval. • If the call is accepted, the MSC sets up the call to the called party following the standard PSTN call setup procedure.
- 37. Call delivery procedure • Step 1. If a wireline phone attempts to call a mobile subscriber, the call is forwarded to a switch, called the originating switch in the PSTN, which queries the HLR to find the current VLR of the MS. (1) The HLR queries the VLR in which the MS resides to get a routable address. (2) If the originating switch is not capable of querying the HLR (i.e., it is not equipped to support mobility), the call is routed through the PSTN to the subscriber's gateway MSC, which queries the HLR to determine the current VLR serving the MS. • Step 2. The VLR returns the routable address to the originating switch through the HLR. • Step 3. Based on the routable address, a trunk (voice circuit) is set up from the originating switch to the MS through the visited MSC.
- 39. Roaming Management under SS7 • The missing parts in the picture are the interactions between the PCS network and the PSTN. • This section briefly describes how mobile roaming is managed by the PSTN signaling.
- 40. Common channel signaling (CCS) • Common channel signaling (CCS) is a signaling method that provides control and management functions in the telephone network. • CCS consists of • supervisory functions • addressing • call information provisioning
- 41. CCS • A CCS channel conveys messages to • initiate and terminate calls • determines the status of some part of the network • controls the amount of traffic allowed. • CCS uses a separate out of band signaling ‑ ‑ network to carry signaling messages.
- 42. SS7 • Signalling System No. 7 (SS7) is a CCS system developed to satisfy the telephone operating companies' requirements for an improvement to the earlier signaling systems, which lacked the sophistication required to deliver much more than plain old telephone service (POTS). • Signaling between a PCS network and the PSTN are typically achieved by the SS7 network.
- 43. SS7
- 44. SS7 • Figure shows the network elements that are involved in the interconnection between a PCS network and the PSTN. In the figure, the dashed lines represent the signaling links; the solid line represents a trunk.
- 45. SS7 • The SS7 network consists of three distinct components: • Service Switching Point (SSP) • Signal Transfer Point (STP) • Service Control Point (SCP)
- 46. Service Switching Point (SSP) • A telephone switch interconnected by SS7 links. The SSPs perform call processing on calls that originate, tandem, or terminate at that node. • A local SSP in the PSTN can be a central office (CO) or end office (EO). • An SSP in a PCS network is called a mobile switching center (MSC).
- 47. Signal Transfer Point (STP) • A switch that relays SS7 messages between network switches and databases. Based on the address fields of the SS7 messages, the STPs route the messages to the correct out going signaling links. To meet the stringent reliability requirements, STPs are provisioned in mated pairs, as shown in Figure.
- 48. Service Control Point (SCP) • Contains databases for providing enhanced services. An SCP accepts queries from an SSP and returns the requested information to the SSP . • In mobile applications, an SCP may contain an HLR or a VLR.
- 49. SS7 • In this network, the trunks (voice circuits) connect SSPs to carry user data/voice information. • The signaling links connect SCPs to STPs, and STPs to SSPs. • The SSPs and SCPs are connected indirectly through STPs.
- 50. Registration • In this example, the MS moves from VLR1 to VLR2. • Step 1. • The MS enters the area controlled by MSC2. • MSC2 launches a registration query to its VLR through STP2, assuming that VLR2 and MSC2 are not co-located.
- 51. Registration • Step 2. • VLR2 sends a registration message to the MS's HLR (HLR4 in Figure 2.8). • VLR2 may not know the actual address of HLR. Instead, VLR2 sends the message containing the MS identity, called the Mobile Identification Number (MIN), to an STP (STP3 in our example) that can translate the MIN into the HLR address. • Step 3. • The MIN to HLR address translation is performed at STP3 ‑ ‑ by a table lookup technique called ‑ global title translation (GTT). STP3 then forwards the registration message to HLR.
- 52. Registration •Step 4. • After the registration, HLR sends an acknowledgment back to VLR2. • Since the address of VLR2 is known, the acknowledgment may be sent to VLR2 using a shortcut, without passing through STP3. •Step 5. • After step 3, HLR sends a deregistration message to VLR1 to cancel the obsolete record. • VLR1 then acknowledges the cancellation (not shown in Figure 2.8).
- 53. Registration •In steps 2, 3, 4, and 5, the messages may visit several STPs before arriving at their destinations, and the registration process may generate considerable traffic in the SS7 network. •Thus, it is desirable to reduce the registration traffic. •Two approaches have been proposed to reduce the "cost" of deregistration at step 5 in Figure 2.8: •implicit deregistration •periodic re-registration
- 54. MSC1 MSC2
- 55. Implicit deregistration • Obsolete VLR records are not deleted until the database is full. • If the database is full when an MS arrives, a record is deleted, freeing storage space to accommodate the newly arrived MS. • A replacement policy is required to select a record for replacement (it is possible that a valid record is replaced, and the information is lost). • Advantage: no deregistration messages are sent among the SS7 network elements.
- 56. Periodic re-registration • The MS periodically reregisters to the VLR. • If the VLR does not receive the re-registration message within a timeout period, the record is deleted. • This approach only creates local message traffic between the MSC and the VLR. Furthermore, no SS7 signaling messages are generated if the VLR is co-located with the MSC.
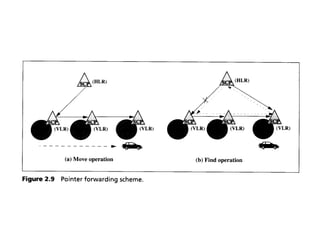
- 57. Pointer Forwarding Scheme • To reduce the registration traffic at steps 2 and 3 in Figure 2.8, a pointer forwarding scheme was proposed, which consists of two operations: • Move operation (registration). • Find operation (call delivery).
- 58. Move operation (registration) • When an MS moves from one VLR to another, a pointer is created from the old VLR to the new VLR. No registration to the HLR is required (see Figure 2.9(a)).
- 59. Find operation (call delivery) • When the HLR attempts to locate the MS for call delivery, the pointer chain is traced. After the find operation, the HLR points directly to the destination VLR (see Figure 2.9(b)).
- 61. Call Delivery • Depending on the memory capacities of the VLRs, the pointers in the obsolete chain may or may not be deleted. • To limit the pointer traversal time in the find operation, the registration procedure in Figure 2.8 may be performed for every k move operations. • In other words, the number of pointers visited in the find operation will be limited by k. The pointer forwarding scheme should not be considered when the new cost of pointer creation and pointer traversal is higher than the cost of accessing the HLR. • As performance studies indicate, the pointer forwarding scheme significantly reduces the network traffic in many cases.
- 62. Call Delivery • Similar to the registration process, visits to several STPs and a GTT may be required to access the HLR in call delivery. • Several STPs may be visited to obtain the routable address from the VLR. • To reduce the call delivery traffic, a cache scheme was proposed to maintain a cache in the originating SSPs. • Another possibility is to maintain the cache in the STP that performs GTTs, that is, STP3 in Figure 2.11. • A cache entry consists of two fields: the MIN of an MS and the address of the current visited VLR of the MS. The cache contains entries for MSs recently accessed from the SSP
- 63. Cache Scheme • When the calling party originates a call to an MS, the SSP first checks if the cache entry for the MS exists. There are three possibilities: • Case 1: The cache entry does not exist. The call delivery procedure illustrated in Figure 2.10 is performed. • Case 2: The cache entry exists and is current. The VLR is directly accessed as shown in Figure 2.11. • Case 3: The cache entry exists but is obsolete. The procedure detects that the cache entry is obsolete if the queried VLR's response is negative. The call delivery procedure illustrated in Figure 2.10 is performed.